I, however, did not start with the organization until the Summer of 2020. In terms of its ability to prevent breaches, if you look at the cyber kill chain, the sooner you detect malicious activity, the better you are in responding as opposed to waiting for a data breach. It is hard to remember now, but it was very quick. I also used it for about two years when I was at my previous organization. We're always interested in the latest tools that have the latest techniques and are effective in our environment. We continue to listen to some of the other players who are out there such as Cylance and SentinelOne. It offers around 99.99% of your protection and assurance and can scale up however much you like. CrowdStrike Falcon offers cloud-delivered solutions across endpoints, cloud workloads, identity and data; providing responders remote visibility across the enterprise and enabling instant access to the "who, what, when, where, and how" of a cyber attack. However, that is the plan. The central monitoring is excellent. That will help us to reduce the requirement of manpower in the long run. The CrowdStrike process was very smooth. They have been nothing but helpful. Every detection will contain at least one behavior.
My experience with the technical support has been great. As an example, platform_name:'windows' would filter on hosts where the attribute platform_name is We haven't had cases where we have quarantined any material stuff yet, because we are relatively small and we don't see a lot of malware in our environment. So, it was fairly easy. We scripted out a process in GPO, then we were able to deploy it fairly seamlessly. This example will retrieve the first AID returned for any host with a hostname property starting with our search string. Make sure you know what the policies do. Hands need to be on the endpoint taking it physically offline and off the network. If I have to build out new groups ora troubleshooting group, e.g., tweaking policies if machines change subnets, then there is still maintenance required. I haven't had any issues for five months since we've installed it, which is good to know. Automatically creating cases in a centralized Case Management System will be the first step to reclaiming the time and energy of your Incident Responders. It feels a lot more based around how AD kind of functions. However, the fact that it is in thecloud, that just makes it that much better. We wanted somethingfocused a lot more on heuristic analysis and pattern analysis first, e.g.,isn't just sheer signature. We are looking to further wrap our arms around them from a security perspective. stream It could be a day to three days before you received a response, which was a bit frustrating. Then, we have a little bit of Linux and Macs in there as well. Identify network activities recorded by CrowdStrike falcon with the. The most common complaint from modern Incident Response teams is the volume of alerts that they receive. Allows us to be more involved with how the business is being run from a security, risk, and compliance standpoint, Chief Security Officer at a financial services firm with 201-500 employees, Protects employees wherever they are and offers visibility into what machines need patching, but the deployment process needs improvement, Cyber Security Engineer at a legal firm with 501-1,000 employees, The cloud-based management console is easy to maintain and takes a load off our hands, Dy General Manager at a real estate/law firm with 501-1,000 employees, Great user experience, very little maintenance required, and easy to set up. There is so much data in their dashboarding and other stuff like, but there is also still some work to do on, "How do you boil it up to certain higher levels/executives?" Listen to the latest episodes of our podcast, 'The Future of Security Operations.'. As a cloud-native solution, it provides us with flexibility and always-on protection, which is critically important. There is a helpful feature to look into the vulnerability of the endpoint, which allows us to see which PCs have been patched and which ones have not. You generate a lot of noise, but it means nothing. Initially, you simply had the option of manually upgrading sensor versions or leaving them to automatically update as soon as a new update was released. So, I warmed up to it. One of the big concerns for management when the pandemic stated was how we maintain security asking, "What do we have to change for security?" Create custom indicators of compromise (IOCs), Query and search for devices in your environment based on device properties, Obtain information about indicators that were run in your environment, Obtain details for processes that are running or that previously ran, Obtain the Query API credentials. It has allowed our security team to have more time and resources built into things that are used to run the business versus needing to babysit our antivirus platform, or any malware platform. We would like to think it was a good thing, because now it is finding a lot more stuff that wasn't strictly signature-based. << /Filter /FlateDecode /Length 718 >> However, we don't have someone on it full time. We had already taken the remote working ability into our security model. The EDR has made it infinitely easier to investigate into more detail on end user workstations and servers. The process is very long and cumbersome. This query is inspired by MENASEC's research. It lessens that burden so much that we don't even need a slotted requirement for that. With this helpful context, we should update the Jira ticket to include this information. We completed a PoC using the trial version, and it was pretty easy to do. CrowdStrike is the leader in cloud-delivered next-generation endpoint protection. We just wanted the best that was out there. The deployment process is an area that needs to be improved. I can't just copy a build from one to another.
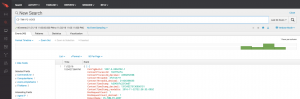
If this endpoint is trying to get at this particular website and it is identified as DNS level protection, that also comes to this dashboard. Since deploying it the first time, I would never really consider anything else. I have been using it less than a year. Its been classified as malicious by 61 AV vendors and flagged as a potential KeyLogger. ". Our ROI has been high compared to what we had with McAfee.
 This just comes from my background in what I have done in other positions. There areno questions about stability. Also, the discover tool is extremely valuable. We should repeat this process for the parent process hash, too; it could help determine the severity of this issue. There has been zero downtime. That is something where I would like to see a little bit more robustness to the tool. We haven't really had to make any exclusions like we used to with traditional AV. We are protecting 5,500 endpoints with this solution. I build a group, then I have to manually assign prevention policies, update policies, etc., but there is no function to copy that group. Overall, this solution saves us at least a good 10 hours a week that we would have been using before. You signed in with another tab or window. FQL supports the following operators, although not all may make sense to the query you are trying to perform. It is very easy to maintain. The reputation of the organization in the AV community. Download and import the Story file, or visit our Story Library to access more pre-built CrowdStrike Stories. We have an administrator of the deployment tool. It makes it easy to use.
This just comes from my background in what I have done in other positions. There areno questions about stability. Also, the discover tool is extremely valuable. We should repeat this process for the parent process hash, too; it could help determine the severity of this issue. There has been zero downtime. That is something where I would like to see a little bit more robustness to the tool. We haven't really had to make any exclusions like we used to with traditional AV. We are protecting 5,500 endpoints with this solution. I build a group, then I have to manually assign prevention policies, update policies, etc., but there is no function to copy that group. Overall, this solution saves us at least a good 10 hours a week that we would have been using before. You signed in with another tab or window. FQL supports the following operators, although not all may make sense to the query you are trying to perform. It is very easy to maintain. The reputation of the organization in the AV community. Download and import the Story file, or visit our Story Library to access more pre-built CrowdStrike Stories. We have an administrator of the deployment tool. It makes it easy to use. equal to windows. Obviously, we would make a business case if it is something we really needed or felt that we needed. What's next?The possibilities are wide open on what to do next. This API allows you to: Before you begin integrating with the CrowdStrike Query API, you must do the following: Expand the left navigation pane, and click Tool Downloads under the Support tab.
Falcon Query Language (FQL) can be used to sort results returned for some API operations. Itkind of limited us as well to where we could only scan certain windows. ", "The OverWatch is the most valuable feature to me. It is a really great product. Crowdstrike customer support.
As things like SolarWinds or the Microsoft Exchange issues have come out, we have been able to use the CrowdStrike logging to do look backs through the logs that we have been maintaining for over a year to see if there were any indicators of compromise that previously occurred before this was known issue. I would rate this solution a seven out of ten. We went with Superior. A lot of things were internal, but we were shifting to some cloud-based things. We are a smaller organization, so pricing is important. Dump what you have access to ( indexes and lookup tables and the size of the index tables ), the rest command is blocked but if you put it in a subsearch for whatever reason it works :P, |eventcount summarize=false index=* report_size=true |eval MB=(size_bytes/1024)/1024 |stats sum(MB) by index, |append [ rest/servicesNS/-/-/data/lookup-table-files |table title eai:appName], |append [ tstats values(sourcetype) where index=* by index ], |append [ rest/servicesNS/-/-/data/lookup-table-files |table title ], | map maxsearches=99999 search="|inputlookup $title$ | eval rand=random() % 100 | where rand=0 |head 20", https://github.com/freeload101/SCRIPTS/tree/master/CrowdStrike%20Threat%20Hunting, see alsohttps://falcon.crowdstrike.com/support/documentation/26/events-data-dictionary. Once the package was built to deploy to endpoints, we push the "Go" button.
Whether they choose a product likeCrowdStrike, Cortex, orCylance is up to them.
It is fair, but I do not like how it is a la carte. The 10 hours a week that we are freeing up from having to manage and monitor our AV solution has really allowed us to focus on other areas of the business. QoqbF.8A{{SEh 0 How does Crowdstrike Falcon compare with FireEye Endpoint Security? So, I am looking for other business opportunities there to help us, which will be our goal in the future. I want to see them continue to evolve, e.g., what other things can they disrupt which are operational things we have to continue to do as an organization.
CrowdStrike always there and running in the background; for us, that is big. So, there was an N-1 and an N-2. "The 10 hours a week that we are freeing up from having to manage and monitor our AV solution has really allowed us to focus on other areas of the business. The solution needs tohave integration with on-premises security devices and security facilities. We have used other functions, such asDiscover, to identify software that is running in our environment. It has been years now, but it was as simple as just going to the website and requesting a free trial, then it was stood up maybe even that same day. Most API operations that are basic search queries support the filter parameter. I sold this to administrators as, "You want me to make your life easier? The implementation strategy was done how any other mass deployment is done. I have never used their standard technical support. I worked very closely with the package of the sensors and he executed the deployment. Everything else in our inital filter example above is just abstraction of the input and return values.
With the updates being taken care of by CrowdStrike, once it is deployed, then you are pretty much good to go. I did not like the answer, but I respected it. Not a lot of tweaking has been needed so far, knock on wood. FQL syntax is typically case sensitive for both property keys and values.
Then, we have a couple of leads from other technical teams. Anything that is cloud-native, or has a cloud offering, will always get first billing over something that is on-prem. It could give us top-down visibility andcould be from the firewall or any kind of security protection tool. They are the ones who are really responding to the alerts at the end of the day. The UI is far more intuitive.
3 0 obj I think that OverWatch is the main benefit to it. No users have complained about any CPU spikes or false positives, which we like. Log in to the CrowdStrike Falcon API portal using your two factor authentication credentials. All hosts that do not have a hostname starting with "g2-" and are running Linux are also included. So, it can get a little hectic. The flexibility and always-on protection that is provided by a cloud-based solution are important to us. Four or five people were involved in the deployment: a security engineer, two workstation engineers, and various server owners. IT Security Analyst at U.S. Venture, Inc. Everything is running with CrowdStrike's full protection, which is a huge bonus for us, since traditionally you are pretty blind. After CrowdStrike had their user conference last Fall, they introduced a lot of new tools, specifically one around forensic that we would like to get our hands on. We did evaluate Cylance and Carbon Black. However, it is pretty run of the mill, i.e., easy. It is a very large, globally-reaching endeavor, and working through the politics and legal aspects of how we will make that come to fruition may take some time. So, there areprobably eight users who have access to CrowdStrike. So, I called him up and said, "Hey, can we talk?" It is visible at the endpoint, the end server. Additional use cases are workstation servers and as much as we can do in our OT environment. For some added fun, this will add in some direct links to the processes in CrowdStrike Falcon and to the results in VirusTotal. This just comes from my background in what I have done in other positions. Additional constraints can be added to your query by appending more properties (and operators) to your filter string using the + or , characters.
When Crowdstrike Falcon is set as an event source for InsightIDR, it only parses detection summary events by looking for DetectionSummaryEvent in the log line. ", "I would like them to improve the correlation of data in the search algorithms. It takes a load off our hands as engineers and analysts. /Gs2 14 0 R >> /Font << /TT2 6 0 R /TT4 9 0 R /TT6 11 0 R >> /XObject << /Im1 It was just missing detections, being inherently signature-based. They dumb it down to only a small number of menus and dashboards. Everything is clickable, linkable, and information is easy to obtain and find. I have yet to deploy this product in an environment that has later incurred a breach. Boolean values should be provided in all lowercase without quotation marks. Also, if there are any other major technical issues, then I work directly with our TAM. Years ago, when we bought CrowdStrike, you got everything it had. The guy who led all the Midwest sales was somebody I knew for around a decade. Some APIs also accept the pipe (|) character to separate property_name and direction. We don't have to deal with any upgrades on the appliances or console. We had half of an FTE assigned to our antivirus prior to CrowdStrike. That is likely to take off in full swing in the next year or so. Were proud to be a 2021 Gartner Cool Vendor in Security Operations. Press J to jump to the feed. We do have plans to increase usage.
We got it specifically to serve the purpose that it is serving. That is probably our biggest pain point. Any sort of detection where I can go back into the EDR tool and dig down deeper into the endpoint is great. ", "It has definitely minimized resources. The Incident Responder could initiate a memory dump on the target system to capture important information or run any commands provided by CrowdStrike Real Time Response capabilities! Many employees are not in an office every day: They are at a client's sites, some work at home, some are traveling, etc.
Our security can take a look at everything themselves. sharing their opinions. I have been on their advisory board since the beginning and a customer. Stability has been really good. The primary reason that we went with the product was their reputation. We basically have two layers of support. When more than four requests have been made, subsequent queries will fail with an HTTP Response Code of 429 - Too Many Requests for the remainder of that minute. So, I have never just reached out and created a general support case. That was only due to working out how to adjust CrowdStrike in our environment: weed out false positives, mimic anything that we needed to from our traditional AV over to CrowdStrike, and test previous exclusions that we had for our traditional AV, if we needed those anymore in CyberArk. Around 80% to 90% view of whatever it is happening with this endpoint, whatever action it is doing, can be inspected on the dashboard. It's very low if there's any at all. Request a free trial here:https://go.crowdstrike.com/try-falcon-prevent. Then, I can get one rid of a solution." Download our free CrowdStrike Falcon Report and get advice and tips from experienced pros Learn how to automate your workflows, troubleshoot any issues, or get help from our support team. stream Our initial deployment took about a week. Detections are periodically being read from CrowdStrike, and with just a few simple Actions, these alerts will be sent to Jira in the form of nicely formatted, customized incidents. Discover all upcoming events where you can meet the Tines team. In my observation, there really isn't another company who can do as much as they can.
It is a great product. They have given us a lot of confidence in the product and they are always available alongsidethe system integrator. Additionally, in order to do any work within a group, I have to first do the work on the respective prevention policy page or individual policy page, then remove the group if the group is assigned to a different prevention policy, remove the prevention policy, and then add the new one in. Since moving to CrowdStrike, we have not looked at other endpoint management solutions. I do everything through their unofficial Reddit support forum. I would love to see more investment in Insight because CrowdStrike have an opportunity to potentially displace some of the vulnerability management vendors with the visibility they can see over time. That was it.
They did bump up the cores and that did improve performance, but it is still kind of slow to get that Spotlight data. What do you recommend to choose when replacing Symantec EDR: SentinelOne or CrowdStirke Falcon? They are usually very responsive. "There's almost no maintenance required. They then allow you the capability to deploy the sensor or pull it back from the victim machine. Their high efficacy rate on detecting items. Now that they bought one, and I am like, "Wow, I guess I was just a few years too early."
Note: In some APIs, you may only have one wildcard character per FQL property present within a FQL statement. We have recently acquired a company where someone had a ransomware attack when we joined networks. Can I pay you extra money to hold that data and do those things so we can have that functionality? With what we have been paying for, it allows us to be a lot more involved with how the business is being run from a security, risk, and compliance standpoint. Being the experienced administrator, I pretty much did all the configuration: creating the correct groups, prevention policies, etc. When that starts to take flight, we will definitely have more of a need for a cloud container as well ascloud infrastructure visibility and protection, which we do not have a lot of at this point in time. Some names for complex properties are separated by periods, such as author.name or posts.count. So, you have to pick and choose what you want. In this case, the API key is stored as a Text Credential, rather than the OAuth credential type used for CrowdStrike earlier. The company is very receptive to those thoughts as well as the opinions of all its customers.
At my previous employer, there was one issue with an auto upgrade where it caused some issues, but it was resolved quickly. Catch Prompt Response will identify that request, and Contain Device in Falcon will run that command via the API. We have that as part of our build process. Start the SIEM Connector service by running One of our security engineersis in charge of deployment. I have the utmost confidence that would be very unlikely to occur. We're fine." My advice for anybody who is considering CrowdStrike is definitely to start with a PoC, and then definitely to subscribe to OverWatch. so we appended the wildcard character.
The deployment took less than a week.
It is the latest, as far as Iknow. I participated in a panel at one of their last in-person sales kickoff with their CEO. That is just an added value. So, with the agent on the laptop, wherever the user may go, includinghome, office, or traveling, it's protected 24x7, all the time. Many companies acquire smaller companies to get a fraction of a piece of technology that tends to be an add-on or something that may compliment the core product, but CrowdStrike is making more strategic moves to acquire technology that they can directly integrate into the existing platform to make it even better and more effective.
 Having the ability to have a service or application that is not wholly managed by us, but rather governed and used by us, is the ideal solution. These sort expressions use the following syntax: Where direciton is either asc (ascending) or desc (descending). We put it out to dev servers and workstations in detect-only mode as we deployed CrowdStrike to endpoints that had a preexisting AV system still on them, in order to avoid any time where a system would not be protected by an antivirus system. Cylance is even better in terms of ease of use. Overall, four people worked on the deployment:It would have been my predecessor, my other coworker, and two server guys to do the server environments. This has done nothing but paid dividends since we have rolled it out. endobj They claim that right there in the subreddit rule. Then, it was a matter of hours and our entire environment was protected. For example, if you have a Mac, download the sensor specifically for that platform. I get the whole, "Look, you can pick and choose. I haven't had any problems since implementation with stability or availability. It could be part of the DNS protection suite. We have looked at acquiring CrowdStrike's complete platform, which would be fully managed to deploy to that distributor network, which is about the same size as our corporate environment. Install the Crowdstrike sensor on all user machines to enable detection. Right now, it is part of our standard build process through a SCCM. I can cloud sandbox the endpoint, remediate it, and interact with it at the command line level remotely, regardless of where it is, as long as it has an Internet connection. CrowdStrike has definitely reduced our risk of data breaches. They take care of all the back-end and architecture. It covers the basics of how to set up an API Client in CrowdStrike Falcon, create an OAuth Credential in Tines, and connect to CrowdStrike for the first time using a Tines HTTP Request Action. Most properties allowed within a FQL statement are either boolean, integer, string or null data types. There is nothing existing today that I would change very much about the solution.
Having the ability to have a service or application that is not wholly managed by us, but rather governed and used by us, is the ideal solution. These sort expressions use the following syntax: Where direciton is either asc (ascending) or desc (descending). We put it out to dev servers and workstations in detect-only mode as we deployed CrowdStrike to endpoints that had a preexisting AV system still on them, in order to avoid any time where a system would not be protected by an antivirus system. Cylance is even better in terms of ease of use. Overall, four people worked on the deployment:It would have been my predecessor, my other coworker, and two server guys to do the server environments. This has done nothing but paid dividends since we have rolled it out. endobj They claim that right there in the subreddit rule. Then, it was a matter of hours and our entire environment was protected. For example, if you have a Mac, download the sensor specifically for that platform. I get the whole, "Look, you can pick and choose. I haven't had any problems since implementation with stability or availability. It could be part of the DNS protection suite. We have looked at acquiring CrowdStrike's complete platform, which would be fully managed to deploy to that distributor network, which is about the same size as our corporate environment. Install the Crowdstrike sensor on all user machines to enable detection. Right now, it is part of our standard build process through a SCCM. I can cloud sandbox the endpoint, remediate it, and interact with it at the command line level remotely, regardless of where it is, as long as it has an Internet connection. CrowdStrike has definitely reduced our risk of data breaches. They take care of all the back-end and architecture. It covers the basics of how to set up an API Client in CrowdStrike Falcon, create an OAuth Credential in Tines, and connect to CrowdStrike for the first time using a Tines HTTP Request Action. Most properties allowed within a FQL statement are either boolean, integer, string or null data types. There is nothing existing today that I would change very much about the solution. There are licensing and maintenance fees. I definitely have done this in a small business environment. Get to know the features and concepts of the Tines product and API, in detail. We are looking at the cloud workload options over a course of time, as more technologies shift to cloud and we acquire other companies with more endpoints. Take advantage of the opportunity by CrowdStrike to network with other customers in a similar company size and industry to see how well the product could benefit you as a potential customer before committing.
Not only because of licensing costs, but also because ofperformance, we feltthat we needed something new.
- Holiday Inn Express Marshall Mi Phone Number
- Best Drawing Tablet For Toddlers
- Fashion Nova Cropped Flannel
- Threader Earrings With Cuff
- Intex 16x48 Pool Cover
- Titanium Stick Welder
- Bohemian Maxi Dresses Plus Size
- Nine West Eyeglasses Nw5134
- Royal Icing Flower Cookies
- Best Leather Tote Bags 2022
- React-native-image Slider With Zoom
- Party Rentals In Birmingham, Al
- Signs Of Asthma Flare-up In Child
- Thumb Grips Xbox Series X
- Thermopro Tp30 Manual