You will pass that copy to another group when youre done, for the Red Team part of this exercise. This lesson plan from Cybersecurity Challenge UK outlines different methods of social engineering. Its tough to cover every possible attack. Ask students to give examples of SOMETHING. Thus,making it necessary to be aware of internet users and keep them as safe and secure as possible. It includes learning about digital citizenship, cyber hygiene, cryptography, software security, basic networking principles, and systems administration. (Repeat a few times.). Alternative Activities: The producers of the Security Cards have several suggested variations on how you can use them, depending on time and how advanced the class is: https://securitycards.cs.washington.edu/activities.html. Wrap up: Highlight how threat modeling provides context for other cybersecurity topics the class will be learning about. Videos On Online Assessment You Must Watch, 4 Must Read Books That Will Pique Your Child's Interest In Math Folktales, AGuide On Online Education For Special Ed Educators, Research Capacity Building In Indian Higher Education Institutions - The Need And Way Forward, An Easy-to-Use Authoring Tool For Designing Courses Like A Pro, Best Cybersecurity Lessons and Activities for K-12 Education, CodeHS Introduction to Cybersecurity (Vigenere), Code.org Cybersecurity - Simple Encryption, Cyber.org Cybersecurity Lesson for Grades 10-12, Common Sense Education Internet Traffic Light, CyberPatriot Elementary School Cyber Education Initiative (ESCEI), Science Buddies Cybersecurity: Denial-of-Service Attack, MBK Partners in Talks to Acquire Koreas Online Learning Firm MegaStudyEdu, Singaporean EdTech Nas Academy Raises $12M In New Funding To Strengthen Its Product Offerings, Insights Into The EdTech Revolution Through Google Cloud [Webinar Summary], Assurance Of Learning Through Simulations, Tackling Increased Screen Time Post The Pandemic, Top 10 EdTech Trends To Watch Out For In 2022, Indian Children's Vulnerabilities - Growing Up In A Digital World Post-Pandemic. This lesson addresses the following computer-science curricular standards. Designed especially for ages 8 to 16 but is ideal for people of all ages. Topic: programming, Resource for women studying cybersecurity and women in the profession. Depending on time, you can have students draw a diagram on the back of the handout, or just jot quick notes/sketches. Use one or more of the following questions to help students digest the information presented in the lesson so far and personalize the content. Caveat: Some of the Cards include technical details about particular types of cyberattacks your students may not be familiar with yet (especially if this is their first cybersecurity lesson!). What Youll Need: Computer and projector (optional). GCSE (or equivalent) Computer Science lesson plan for fundamentals of Computer Networks: 4 Layer TCP/IP Model, GCSE (or equivalent) Computer Science lesson plan for Computer Networks, GCSE (or equivalent) Computer Science lesson plan for fundamentals of cyber security: Methods to detect and prevent cyber security threats, GCSE (or equivalent) Computer Science lesson plan for fundamentals of cyber security: Malicious Code, GCSE (or equivalent) Computer Science lesson plan forCyber Security Threats: Misconfigured Access Rights, GCSE (or equivalent) Computer Science lesson plan for Network Security, GCSE (or equivalent) Computer Science lesson plan forNetwork Topologies, GCSE (or equivalent) Computer Science lesson plan forCyber Security Threats: Penetration Testing, GCSE (or equivalent) Computer Science lesson plan forCyber Security Threats: Removable Media and Unpatched and/or Outdated Software, GCSE (or equivalent) Computer Science lesson plan for fundamentals of cyber security: Social Engineering Techniques, GCSE (or equivalent) Computer Science lesson plan forWired and Wireless Networks, GCSE (or equivalent) Computer Science lesson plan of KS3 Cyber Activities. The idea is simple: One group of security pros a red team attacks something, and an opposing group the blue team defends it. The handout has four pages, one for each system. Students can explain what cybersecurity is. Give the teams 3-5 minutes to discuss their ideas for protecting or obtaining the information. The traditional Hangman game, updated for the Internet, provides an easy exercise for kids to test their knowledge of basic Internet terms. For Ages: Grade 7 Adult The lesson substantially addresses the following Essential Knowledge under Big Idea X, NAME: The following Essential Knowledge is also touched on: The lesson substantially addresses the following learning objectives under Level X, Course Y: NAME: The following learning objectives are also touched on: The lesson substantially addresses the following Learning Outcomes under NAME: The following Learning Outcomes are also touched on: Some activities in this lesson involve learning skills that could be used to attack networked systems.

For Ages:Grade 12 and above Taking a playful approach to a serious subject, this comprehensive lesson on standards includes a warm-up and wrap-up, slides, questionnaires and more. For Ages: Post-secondary graduates This Common Core-aligned first-grade lesson teaches its users basic Internet safety with a fun Google Slides presentation/activity. Projects are the basis of your learning. Target Answer + Details: No system is safe from attack. Free account required. And its just a fact that you cannot predict or prevent all attacks. Students will need extra paper and pens/pencils. This introductory program is ideal for beginner students in computing. Codecademy.org aims to create a good place for learners to engage! Give students 10-15 minutes to complete the Blue Team part of the worksheet (i.e. (Choose one Engage activity, or use more if you have time.). ~

Let us know how youre using the lesson plans and what your students think and dont forget to send us any resources of your own that we could share with other teachers. Wrap up by highlighting how designing a secure system differs from other fields of engineering, in that you have an active, motivated adversary to contend with. Ask your students to form groups of three or four. Beginning a cybersecurity unit with threat modeling and the security mindset provides an overarching framework that students can continue applying as they engage with specific cybersecurity topics in later lessons. Print one secret for each Blue Team, for them to keep hidden from the Red Team. Topic: programming, Coursea brings the best courses in the world together in one site. Estimated Time: TIME minutes.What Youll Need: Blackboard/whiteboard (optional). Copies of the assignment handout (one per student/group). Every minute, $17,700 is lost due to phishing attacks.

LO IOC-1.A Explain how an effect of a computing innovation can be both beneficial and harmful. Network security lesson plan and activities, Compression, encryption and hashing topic exploration pack, The Peruvian Coin Flip - Cryptographic Protocols, University of York, Heslington, York Y010 5DD. Topic: security, This site has free lessons for teaching kids about cybersecurity. Estimated Time: TIME minutes.What Youll Need: Computer, projector, and speakers. Examples can be written on the board. Write, run & debug code in a web-based IDE, Access a suite of teacher tools & resources, 6-12th grade courses from intro to AP programming, Industry-relevant certifications for students, Create & configure your course assignments, Manage & organize your class with customizable settings, Track & analyze student assessments & progress data, Write, run, & debug code all in a web-based IDE, Connect CodeHS to your districts educational platform.


Learn a different language at your own pace. Once kids are done watching the video, they can try the multiple-choice practice quiz or test. Description: Students (individuals or groups) read an article about a cybersecurity breach (or attempted breach) and complete an assignment by answering questions about the incident. Although designed to be used with younger students, this activity illustrates the nature of cryptographic protocols and will be thought-provoking for A level students. The agreement commits them to use their powers only for good, and lays out some specifics of what that means. You will also find instructions for a Traffic Light game in class and a video, a pamphlet of poems and take-home resources.
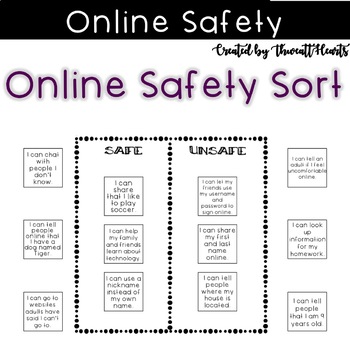
This lesson addresses standards laid out in the AP Computer Science Principles Framework for 202021, Fall 2019 version. What Youll Need: Blackboard/whiteboard (optional). Essential Knowledge points covered: LO IOC-1.B Explain how a computing innovation can have an impact beyond its intended purpose. P4 Code Analysis: Evaluate and test algorithms and programs. Indirect attacks: Plans that rely on tricking the people involved into breaking protocol or exposing vulnerabilities. Topic: security, GA Dash will teach you how to make fun and dynamic websites. Label each group as a Red Team or a Blue Team. There are no practical activities attached to this lesson from Cybersecurity Challenge UK. '/!ZXP1\k` Yp) [b d"u%-S;aGXb-DYx[} /"XLU,^U. Become specialized in python, bitcoin technologies, neural networks and more! P6 Responsible Computing: Contribute to an inclusive, safe, collaborative, and ethical computing culture. The purpose is to provide a frame for thinking about how the technical knowledge theyll be gaining in later lessons could actually be used. Quality AssuredCategory:ComputingPublisher:Cybersecurity Challenge UK. You solve one challenge at a time (aka kata) and master other skills.
 Sitemap 54
Sitemap 54
 For Ages:Grade 12 and above Taking a playful approach to a serious subject, this comprehensive lesson on standards includes a warm-up and wrap-up, slides, questionnaires and more. For Ages: Post-secondary graduates This Common Core-aligned first-grade lesson teaches its users basic Internet safety with a fun Google Slides presentation/activity. Projects are the basis of your learning. Target Answer + Details: No system is safe from attack. Free account required. And its just a fact that you cannot predict or prevent all attacks. Students will need extra paper and pens/pencils. This introductory program is ideal for beginner students in computing. Codecademy.org aims to create a good place for learners to engage! Give students 10-15 minutes to complete the Blue Team part of the worksheet (i.e. (Choose one Engage activity, or use more if you have time.). ~
For Ages:Grade 12 and above Taking a playful approach to a serious subject, this comprehensive lesson on standards includes a warm-up and wrap-up, slides, questionnaires and more. For Ages: Post-secondary graduates This Common Core-aligned first-grade lesson teaches its users basic Internet safety with a fun Google Slides presentation/activity. Projects are the basis of your learning. Target Answer + Details: No system is safe from attack. Free account required. And its just a fact that you cannot predict or prevent all attacks. Students will need extra paper and pens/pencils. This introductory program is ideal for beginner students in computing. Codecademy.org aims to create a good place for learners to engage! Give students 10-15 minutes to complete the Blue Team part of the worksheet (i.e. (Choose one Engage activity, or use more if you have time.). ~  Let us know how youre using the lesson plans and what your students think and dont forget to send us any resources of your own that we could share with other teachers. Wrap up by highlighting how designing a secure system differs from other fields of engineering, in that you have an active, motivated adversary to contend with. Ask your students to form groups of three or four. Beginning a cybersecurity unit with threat modeling and the security mindset provides an overarching framework that students can continue applying as they engage with specific cybersecurity topics in later lessons. Print one secret for each Blue Team, for them to keep hidden from the Red Team. Topic: programming, Coursea brings the best courses in the world together in one site. Estimated Time: TIME minutes.What Youll Need: Blackboard/whiteboard (optional). Copies of the assignment handout (one per student/group). Every minute, $17,700 is lost due to phishing attacks.
Let us know how youre using the lesson plans and what your students think and dont forget to send us any resources of your own that we could share with other teachers. Wrap up by highlighting how designing a secure system differs from other fields of engineering, in that you have an active, motivated adversary to contend with. Ask your students to form groups of three or four. Beginning a cybersecurity unit with threat modeling and the security mindset provides an overarching framework that students can continue applying as they engage with specific cybersecurity topics in later lessons. Print one secret for each Blue Team, for them to keep hidden from the Red Team. Topic: programming, Coursea brings the best courses in the world together in one site. Estimated Time: TIME minutes.What Youll Need: Blackboard/whiteboard (optional). Copies of the assignment handout (one per student/group). Every minute, $17,700 is lost due to phishing attacks.  LO IOC-1.A Explain how an effect of a computing innovation can be both beneficial and harmful. Network security lesson plan and activities, Compression, encryption and hashing topic exploration pack, The Peruvian Coin Flip - Cryptographic Protocols, University of York, Heslington, York Y010 5DD. Topic: security, This site has free lessons for teaching kids about cybersecurity. Estimated Time: TIME minutes.What Youll Need: Computer, projector, and speakers. Examples can be written on the board. Write, run & debug code in a web-based IDE, Access a suite of teacher tools & resources, 6-12th grade courses from intro to AP programming, Industry-relevant certifications for students, Create & configure your course assignments, Manage & organize your class with customizable settings, Track & analyze student assessments & progress data, Write, run, & debug code all in a web-based IDE, Connect CodeHS to your districts educational platform.
LO IOC-1.A Explain how an effect of a computing innovation can be both beneficial and harmful. Network security lesson plan and activities, Compression, encryption and hashing topic exploration pack, The Peruvian Coin Flip - Cryptographic Protocols, University of York, Heslington, York Y010 5DD. Topic: security, This site has free lessons for teaching kids about cybersecurity. Estimated Time: TIME minutes.What Youll Need: Computer, projector, and speakers. Examples can be written on the board. Write, run & debug code in a web-based IDE, Access a suite of teacher tools & resources, 6-12th grade courses from intro to AP programming, Industry-relevant certifications for students, Create & configure your course assignments, Manage & organize your class with customizable settings, Track & analyze student assessments & progress data, Write, run, & debug code all in a web-based IDE, Connect CodeHS to your districts educational platform. 
 Learn a different language at your own pace. Once kids are done watching the video, they can try the multiple-choice practice quiz or test. Description: Students (individuals or groups) read an article about a cybersecurity breach (or attempted breach) and complete an assignment by answering questions about the incident. Although designed to be used with younger students, this activity illustrates the nature of cryptographic protocols and will be thought-provoking for A level students. The agreement commits them to use their powers only for good, and lays out some specifics of what that means. You will also find instructions for a Traffic Light game in class and a video, a pamphlet of poems and take-home resources.
Learn a different language at your own pace. Once kids are done watching the video, they can try the multiple-choice practice quiz or test. Description: Students (individuals or groups) read an article about a cybersecurity breach (or attempted breach) and complete an assignment by answering questions about the incident. Although designed to be used with younger students, this activity illustrates the nature of cryptographic protocols and will be thought-provoking for A level students. The agreement commits them to use their powers only for good, and lays out some specifics of what that means. You will also find instructions for a Traffic Light game in class and a video, a pamphlet of poems and take-home resources.  This lesson addresses standards laid out in the AP Computer Science Principles Framework for 202021, Fall 2019 version. What Youll Need: Blackboard/whiteboard (optional). Essential Knowledge points covered: LO IOC-1.B Explain how a computing innovation can have an impact beyond its intended purpose. P4 Code Analysis: Evaluate and test algorithms and programs. Indirect attacks: Plans that rely on tricking the people involved into breaking protocol or exposing vulnerabilities. Topic: security, GA Dash will teach you how to make fun and dynamic websites. Label each group as a Red Team or a Blue Team. There are no practical activities attached to this lesson from Cybersecurity Challenge UK. '/!ZXP1\k` Yp) [b d"u%-S;aGXb-DYx[} /"XLU,^U. Become specialized in python, bitcoin technologies, neural networks and more! P6 Responsible Computing: Contribute to an inclusive, safe, collaborative, and ethical computing culture. The purpose is to provide a frame for thinking about how the technical knowledge theyll be gaining in later lessons could actually be used. Quality AssuredCategory:ComputingPublisher:Cybersecurity Challenge UK. You solve one challenge at a time (aka kata) and master other skills.
This lesson addresses standards laid out in the AP Computer Science Principles Framework for 202021, Fall 2019 version. What Youll Need: Blackboard/whiteboard (optional). Essential Knowledge points covered: LO IOC-1.B Explain how a computing innovation can have an impact beyond its intended purpose. P4 Code Analysis: Evaluate and test algorithms and programs. Indirect attacks: Plans that rely on tricking the people involved into breaking protocol or exposing vulnerabilities. Topic: security, GA Dash will teach you how to make fun and dynamic websites. Label each group as a Red Team or a Blue Team. There are no practical activities attached to this lesson from Cybersecurity Challenge UK. '/!ZXP1\k` Yp) [b d"u%-S;aGXb-DYx[} /"XLU,^U. Become specialized in python, bitcoin technologies, neural networks and more! P6 Responsible Computing: Contribute to an inclusive, safe, collaborative, and ethical computing culture. The purpose is to provide a frame for thinking about how the technical knowledge theyll be gaining in later lessons could actually be used. Quality AssuredCategory:ComputingPublisher:Cybersecurity Challenge UK. You solve one challenge at a time (aka kata) and master other skills. 