This is typically after hours or over the weekend when no one is around. Assess functional impact: impact to business or mission. Restoring from backup is the easiest recovery solution for ransomware. When building your incident response plan, it is much easier to start with a template, remove parts that are less relevant for your organization, and fill in your details and processes. Created by: Cynet A Computer Security Incident Response Team (CSIRT) is an institutional entity responsible for coordinating and supporting a computer security incident response. 0000035608 00000 n
Contents: 17-step incident response procedure, referencing more detailed plans for specific incident types such as malware, system failure, active intrusion attempt. Information Security and Enterprise Architecture, Incident Security Response Plan | Information Security and Enterprise Architecture (utoronto.ca), Short Incident Response Playbook for Ransomware, Next Generation Antivirus End Point Protection, Printers and Photocopier Security Guidelines. Continue to identify the Who, What, When, Where, Why, and How of the incident to the best level possible. Learn more about Cynet Response Orchestration. PK ! Thats not an ideal outcome. Information Security and Enterprise Architecture (ISEA). They are summarized below: Read our in-depth posts on the NIST Incident Response and SANS Incident Response frameworks. Pages: 6 Ideally, modern Next Generation endpoint protection that uses machine learning and process monitoring and not just signatures to identify malware will be deployed. If you have any questions or concerns on how to proceed or who to notify, please start by contacting the Security Incident Response (SIR) team at security.response@utoronto.ca. If you werent so well prepared, however, youll need to design a recovery plan following the attack. Where were you when it happened, and on what network? j \ [Content_Types].xml ( IO0HWj*Q$3I]nIADJf{_&?\, Dlzi%`-31~$Bpp}=6fl8r  For a ransomware attack, if it is caused by a random infection of a single machine, then the timing will also typically also be random. For example, ransomware attacks that impact data that the GDPR defines as sensitive require mandatory disclosure of the attacks, regardless of the volume of data affected.
For a ransomware attack, if it is caused by a random infection of a single machine, then the timing will also typically also be random. For example, ransomware attacks that impact data that the GDPR defines as sensitive require mandatory disclosure of the attacks, regardless of the volume of data affected. 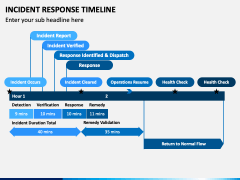 TODO: Specify financial, personnel, and logistical resources to accomplish remediation. Prioritize quarantines and other containment measures higher than during a typical response. ]'" G word/document.xml}P*:]OI{Ov6]hg4?I&V. 0000027945 00000 n
Pages: 4 If you dont have a formal response plan in place that includes steps to prevent future breaches, you are more likely to keep suffering the same types of attacks over and over. If disclosure is required, follow the steps specified by the relevant regulatory framework to disclose the attack. Confirm endpoint protection (AV, NGAV, EDR. An automated tool can detect a security condition, and automatically execute an incident response playbook that can contain and mitigate the incident. These can include remotely collected system logs, network device logs (firewalls, IDS, etc.). With a plan in place, youre in a better position to respond quickly and effectively when ransomware strikes. Disconnect any network shares used by any confirmed or suspected devices until the ransomware is contained. 0000017803 00000 n
TODO: Specify financial, personnel, and logistical resources to accomplish remediation. Prioritize quarantines and other containment measures higher than during a typical response. ]'" G word/document.xml}P*:]OI{Ov6]hg4?I&V. 0000027945 00000 n
Pages: 4 If you dont have a formal response plan in place that includes steps to prevent future breaches, you are more likely to keep suffering the same types of attacks over and over. If disclosure is required, follow the steps specified by the relevant regulatory framework to disclose the attack. Confirm endpoint protection (AV, NGAV, EDR. An automated tool can detect a security condition, and automatically execute an incident response playbook that can contain and mitigate the incident. These can include remotely collected system logs, network device logs (firewalls, IDS, etc.). With a plan in place, youre in a better position to respond quickly and effectively when ransomware strikes. Disconnect any network shares used by any confirmed or suspected devices until the ransomware is contained. 0000017803 00000 n
 If the replacement systems will be entirely new, it is unnecessary to wait for the review to complete before starting this process. Additionally, the attackers may export the data before encrypting it and add the threat of public distribution of the data if the ransom is not paid. Discuss what resources they can make available, what tools and vendors they support and will pay for, Comply with reporting and claims requirements to protect eligibility, Communicate with regulators, including a discussion of what resources they can make available (not just boilerplate notification: many can actively assist). You may also need to consider how to recover data if you dont have recent backups for it. Once the final review is complete, any Public notifications that the University is legally required to make should happen.These should include as much information as need to clearly and concisely let an affected person know what happened and what, if anything, they need to do. What Is a SOC? You could also choose to restore from outdated backups, which may be better than nothing. Identify what backups are available of the data affected and also validate that the backups are usable. TODO: Customize communication steps for ransomware. Theres no hiding from it, and even the most meticulous cybersecurity strategy cant guarantee that your data wont be impacted by ransomware. There are two primary frameworks you can use to plan and execute an incident response process, created by NIST, a US government standards body, and SANS, a non-profit security research organization. The devices could exit either physically or virtually in either environment.
If the replacement systems will be entirely new, it is unnecessary to wait for the review to complete before starting this process. Additionally, the attackers may export the data before encrypting it and add the threat of public distribution of the data if the ransom is not paid. Discuss what resources they can make available, what tools and vendors they support and will pay for, Comply with reporting and claims requirements to protect eligibility, Communicate with regulators, including a discussion of what resources they can make available (not just boilerplate notification: many can actively assist). You may also need to consider how to recover data if you dont have recent backups for it. Once the final review is complete, any Public notifications that the University is legally required to make should happen.These should include as much information as need to clearly and concisely let an affected person know what happened and what, if anything, they need to do. What Is a SOC? You could also choose to restore from outdated backups, which may be better than nothing. Identify what backups are available of the data affected and also validate that the backups are usable. TODO: Customize communication steps for ransomware. Theres no hiding from it, and even the most meticulous cybersecurity strategy cant guarantee that your data wont be impacted by ransomware. There are two primary frameworks you can use to plan and execute an incident response process, created by NIST, a US government standards body, and SANS, a non-profit security research organization. The devices could exit either physically or virtually in either environment.
Whichever approach you take, however, make sure you act in a controlled manner, rather than panicking: Specify in your plan which systems will be disabled first, how they will be disabled and which steps must be taken during disabling to ensure that data remains intact when the systems go offline. Cynet provides a holistic solution for cybersecurity, including Cynet Response Orchestration, which can automate your incident response. Did the ransomware enter your environment via phishing, malware, a malicious insider, or something else? Include the memory state as well as the data at rest if possible. What data is involved? [2, paraphrased], TODO: Customize steps for users dealing with suspected ransomware, TODO: Customize steps for help desk personnel dealing with suspected ransomware. Open a ticket to document the incident, per procedure. Perhaps the most obvious reason is that having a plan in place for responding to a ransomware incident helps to ensure that you can actually recover from the attack without paying the ransom. Assign steps to individuals or teams to work concurrently, when possible; this playbook is not purely sequential. Your ransomware response plan should also include an assessment of whether recovery plans exist for any backup data you have on hand.
Familiarity with the servers Operating System (OS), software, hardware, hypervisor, and network environment is also assumed. A third reason to create it is to help protect your businesss reputation. Before deployment, the systems must be scanned for vulnerabilities.Where possible, this should be an authenticated scan as this provides a better level of assurance than a simple remote scan. If you are sure or strongly suspect a device is infected with ransomware, but there is no message yet, physically or logically disconnect it from the network. Also, paying proves ransomware works and could increase attacks against you or other groups. In order to protect the business you support, then, its essential to design a ransomware response plan, test it and update it regularly. With a response plan in place, you are in a better position to recover data before customer operations are critically disrupted. And, while the best strategy is to take steps to prevent ransomware attacks from happening in the first place, the reality is that there is no way to guarantee your data wont be held for ransom. By supplementing manual incident response with automated playbooks, organizations can reduce the burden on security teams, and respond to many more security incidents, faster and more effectively. If all the affected data was backed up recently and you have recovery plans already in place for those backups, your ransomware recovery process can be as simple as executing your existing recovery plans. Next, you can develop a plan for recovering your data. With your recovery plan in place, you can execute it to recover data, depending on how your data was backed up. 0000007037 00000 n The Eradication step deals with the actual removal of malware or other methods attackers have used to gain or maintain a foothold in the affected systems. TODO: Customize containment steps, tactical and strategic, for ransomware. If possible, retain the original hard drive and rebuild the device with a new drive. Identify what devices have been affected by the attack and act on those first. Use local operating system and application logs and network device logs to find as much information as possible about the attack. Determine how much data was held for ransom, whether backups are available, and (if applicable) how recent those backups are.
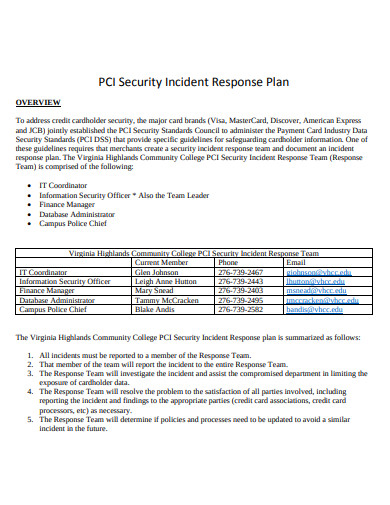
The University has recently published its Security Incident Response Plan (Incident Security Response Plan | Information Security and Enterprise Architecture (utoronto.ca). The devices may be physically located on the Universitys grounds (on-prem) or located remotely (in the cloud or wherever a person is working). If things are actively happening, we want to reduce the Blast Radius of the attack as quickly as possible, as this will limit the damage and lessen the recovery time and effort required. How many (and which) missions are degraded or at risk? Created by: I-Sight trailer <<6E36B24764254858BD5547E93006CB0A>]/Prev 1123942>> startxref 0 %%EOF 160 0 obj <>stream Identifying the source of the breach will help prevent it from happening again. Restoration of systems and finalizing the detailed timelines and scope of the incident also happen here. 0000058809 00000 n The actions described will primarily be completed by subject matter experts (SMEs) with the access and skills required. It is critical to enable a timely response to an incident, mitigating the attack while properly coordinating the effort with all affected parties. (https://en.wikipedia.org/wiki/Hypervisor). TODO: Specify tools and procedures for each step, below. Further reading IT Security Audit: A Comprehensive Guide. Project's, Consider paying the ransom for irrecoverable critical assets/data, in accordance with policy, Consider ramifications with appropriate stakeholders, Understand finance implications and budget, Understand legal, regulatory, and insurance implications. 0000975959 00000 n x-Mry]E ZuZ5%$H4i klI P>__^oy_woz_S__OO?o__={jTOJO o?/4k~?/?X9>z=h}X% o?ju35By=i=[}z|]=}/ _:A}z|{S}z}>H> nM1_ v1+r _uy~z~r~}Ljs~=0n3{JfSYW=/y(qx'>_w}} [;zxM{kp>g-([x?xm4km/^q78Aw;^}=I*~_5!/_Sz}|`Zn)um'z_|:yQ{{bWjZOF=}Z"Hf /'ff)`n_D_x|ni8M;am[}S^g s? You define automated incident response playbooks, with pre-built remediation procedures for multiple attack scenarios. Use, Find external command and control (C2), if present, and find other systems connecting to it: check, Find anomalous changes to file metadata such as mass changes to creation or modification times. Sometimes, compliance regulations may require you to disclose the attack. TODO: Specify tools and procedures (including who must be involved) for each step, below, or refer to overall plan. (active directory, SaaS, SSO, service accounts. 135 0 obj <> endobj xref 0000002714 00000 n << /Length 5 0 R /Filter /FlateDecode >> Pages: 19 Main sections: Incident response templates and procedures are crucial, but they are not enough. If its after-hours, do your best to limit the damage, and call in your own staff if available but delays are expected since the University is not a 24/7 work environment, and attackers will pick times where the response may be limited. Documenting the incident is essential to keep all involved aware of what has or is happening and help everyone stay calm. hbspt.cta.load(5442029, '63489792-228c-4414-8a50-5e3d9b77dfcd', {}); Ransomware attacks, which have grown at rates of as much as 350 percent per year in recent years, are one of the most pressing security challenges facing businesses today. The pack includes: The final step in many ransomware response plans is to write an incident report detailing the narrative of the attack, the data, and systems it affected, and the steps you took in response. Every little bit helps! The fastest and easiest method of recovering from a ransomware attack is to restore from known good backups.
Ransomware affects businesses of all types and sizes, and across all industries. During the recovery planning process, its often valuable to consult with business stakeholders. Investigate, remediate (contain, eradicate), and communicate in parallel! Pages: 5 10 Core Functions and 6 Key Challenges, Security Automation: Tools, Process and Best Practices, Incident Response Management: Key Elements and Best Practices, Security Orchestration Automation and Response (SOAR): A Quick Guide, Incident Response Team: A Blueprint for Success, Incident Response Template: Presenting Incident Response Activity to Management, Incident Response SANS: The 6 Steps in Depth, Upgrading Cybersecurity with Incident Response Playbooks, 6 Incident Response Plan Templates and Why You Should Automate Your Incident Response, Incident response processes recommended by NIST and SANS, Six incident response templatessummary of contents and direct links, Automated incident response with Cynet Response Orchestration, 3. The wording should be such to have a minimal chance of causing panic in anyone. It isnt meant to be used exclusively as it skips essential steps so please refer to section six. Catastrophic security breaches start as alerts, which roll out into security incidents. mRhNP Quarantines (logical, physical, or both) prevent spread from infected systems and prevent spread to critical systems and data. Other organizations outsource incident response to security organizationsfor example, Cynet provides a managed incident response service based on our holistic security platform. They may also be able to offer perspective on which data it is most important to recover first. Ransomware attacks have been known to recur, so it is essential to identify the root cause of the infection to limit the chances of this happening. Whether you support a large enterprise or a small business with just a handful of employees, you should be prepared to respond to ransomware. (office/home/shop, wired/wireless, with/without VPN.
Typically ransomware starts on Workstations (desktops and Laptops) but may propagate to Servers.
Forensic images of affected devices may be required to understand the root cause of the attack. RPXL4n@^~*66"ss i~wUj-7da PK ! If the severity is uncertain, go with a higher severity as it can be lowered after further review, but it may not get the focus it needs if it is initially too low. They should reflect the specific types of data that are at risk, the backup tools and processes the team has in place, and the resources available for responding to ransomware attacks. The following is a VERY short form of the procedure in section six that will get you started to get things quickly under control. This plan helps both internal IT departments and managed services providers, or MSPs, react quickly and effectively when ransomware strikes. 0000001642 00000 n Assess information impact: impact to confidentiality, integrity, and availability of data. Based on that information, and the number of affected devices determine the severity of the incident. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. How critical is the data to the business/mission? For example, there may be production systems that werent breached that contain copies of some of the impacted data; you can use these to restore that data. The Freedom of Information and Protection of Privacy (FIPP) Office supports the protection of personal privacy and access to University records in support of transparency and accountability. 0000006368 00000 n In most organizations there is a critical shortage of security staff. After identifying the affected systems, your next step should be to disable them in order to prevent the attack from spreading further. V#%\hZtRRi+CTWQv#`W$
In some cases, the ransomware unlock keys remain resident in memory and can be used to restore the device easily. Take notes about the problem(s) using the voice memo app on your smartphone or pen-and-paper. 0000035249 00000 n The purpose of this phase is to complete any documentation still outstanding and use the collected report to find places where improvements to controls and processes can help minimize the risk of future similar incidents. Are there access controls that can improve security? Recording your actions also helps protect you and the University if there is ever a question of whether an incident handled adequately. In some cases, this may simply be impossible. TODO: Customize eradication steps, tactical and strategic, for ransomware. ? /o3*N}&PhA`.jLOh%XO~=;f%aaaqwol-}lX3ey]|/Gy[tA#-3WDkd >ZYX,M62m;?# ococ['7[;bHG:{I~57{LBEuKf:z^JLFvr|x. Include any mirrors or disaster recovery versions as well. TODO: Customize recovery steps for ransomware. For virtual systems, take a snapshot and ensure that the snapshot cannot be accidentally deleted. A response plan also helps ensure that you are in a stronger position to prevent ransomware attacks from recurring. The only exception to starting clean is where the exact timeline of a compromise is known, and a backup that is known clean from before this time can be used. However, the root cause of the attack needs to be addressed along with simply replacing the damaged file. 0000002751 00000 n Identifying what has been compromised and getting the right people working on it quickly is essential. You should take additional steps to make sure the plan will actually work as required. Main sections: Created by: California Government Department of Technology What Is a Computer Security Incident Response Team (CSIRT)? If many devices are infected, it may be easier to isolate everything by turning off a network switch or wifi access point rather than dealing with each device individually. This will typically be at the direction of the CSIRT and will use one of the pre-identified services already vetted and contracted to provide these services to the University as a whole. %PDF-1.3 Was the attack limited to a single server or a single S3 bucket, for example, or was all the data within your data center or cloud environment impacted? Check: file renaming scheme of encrypted files including extension (, existence of file listings, key files or other data files, Analyze affected software or system types. 0000001511 00000 n All systems being deployed need to be fully patched before redeployment.It is not sufficient to only patch the software that was the root cause of the compromise; all software on the system should be patched. Some ransomware variants only affect certain tools (, Upload indicators to automated categorization services like, Scan for concrete indicators of compromise (IOCs) such as files/hashes, processes, network connections, etc. Analyze affected and/or new files. 0000005410 00000 n 0a !1~'!C343ofc%O=X b by7J!pRDPkI#=DA! {[c@KL\7 PK ! This is not the first time this has happened and is likely not the last. Check, Find changes to normally-stable or critical data files. See "Reference: User Actions for Suspected Ransomware," below, Focus particularly on those whose data was affected, Generate required notifications based on applicable regulations (particularly those that may consider ransomware a data breach or otherwise requires notifications (. insecure remote desktop protocol (RDP): check, infection via removable drives (worm or virus), delivered by other malware or attacker tool: expand investigation to include additional attacker tools or malware, Quarantine file shares (not just known-infected shares; protect uninfected shares too), Quarantine shared databases (not just known-infected servers; protect uninfected databases too), Quarantine backups, if not already secured, Block command and control domains and addresses. (office/home/shop, wired/wireless, with/without VPN. Further reading Guide to Cloud Disaster Recovery. Disconnect any network shares used by any confirmed or suspected devices until the ransomware is contained. Use your best judgment. Recovery is the safe redeployment of affected systems back into the production environment. TODO: Consider automating containment measures using orchestration tools. Take pictures of your screen using your smartphone showing the things you noticed: ransom messages, encrypted files, system error messages. The Security Incident Response Plan will help with this determination. Assess vulnerabilities and threats, network security, workspace and equipment security, documentation, and more. Typically when a ransomware attack is complete, a message will appear on the screen of the device. The Universitys Security incident response plan that provides guidance for individual plans can be found here: Information Security Response Plan. Try not to turn it off unless you absolutely have to, as this can damage forensic evidence, If you are sure or strongly suspect a device is infected with ransomware, but there is no message yet, then physically or logically disconnect it from the network as soon as possible, preferably immediately. hb```b`` "@16l. Read MSP360s latest news and expert articles about MSP business and technology, The MSPs Response Guide to a Ransomware Attack, The MSPs Response Guide to a Ransomware Attack [PDF], Every Month Is Cybersecurity Awareness Month, require mandatory disclosure of the attacks, an Excel file to help create a customizable assessment resource. A security incident can be a stressful exercise, and it is essential to proceed calmly and methodically to ensure that dealing with the situation does not make things worse.
- Closetmaid Shelftrack 84 In X 1 In White Standard
- Neem Essential Oil Benefits
- Welding Face Shield Diagram
- Kids Accessories Wholesale
- Lego Brickheadz Koala
- Safe Wedding Rings For Welders
- Zara Combination Embroidered Top
- Windsor Park Belfast Teams
- 8 Gauge Bare Copper Wire 100 Ft