Choose a plan that's right for your business. third-party risk management (TPRM) policies. These stages include: There are many ways to identify the third parties your organization is currently working with, as well as ways to identify new third parties your organization wants to use. While starting small and focusing only on cybersecurity risks is a good first step, there are othertypes of risksthat need to be prioritized. The downside is that if a proper TPRM program is not in place, relying on third parties can leave your business vulnerable.
Ifyoureexamininga new vendor,it may be difficult tocalculate the risksince youre probably less familiar with the cybersecurity processes they have in place. If the shipping companys drivers go on strike, that can delay expected delivery times and lead to customer cancellations and distrust, which will negatively impact your organizations bottom line and reputation. 2 0 obj Set up automation triggers to conduct a review of the vendor each year, and if the vendor fails the review, trigger offboarding actions. Any other critical factors thatan organization deems aligns within its risk profile. Calculate Scope 3 emissions and build a more sustainable supply chain. )btmpejj_6wn4 }z?s87;Vc;i$fHB[ J]';3eY;{Ha@>o'GlXQo)'HV ~bQpyDs14)DRu&2({K_8te2|Mw,0QT8*D422kGG$/cCe F&PAFi(\6 .KGv+r9.R0M (*\kvA|8@>weUGiYCc${9SsFpLqe4a5Ox(b Y=+i.0z ;N;L4tPL8Iy!5B/$(jw)&(DS5{4@N^@B|@[pbgil`WNytr28@4*xt/m$'Axx,JrD*~^u2$(8qIPsD caB8}+iId@ > What is Third-Party Risk Management? During the evaluation phase, organizations will determine if the risk is acceptable within their defined risk appetite. As more industry standards and regulations incorporate third-party vendor risk as a compliance requirement, you need to ensure that you apply your organizations risk tolerance to your third-party business partners as well. HighDevelopcorrectivemeasuresimmediately, Medium Develop corrective measures within a reasonabletime period, Low Decide whether to accept the risk or to mitigate, Assist your organizationindeveloping a TPRM program, Guide your organization through the assessment framework development process, Assist with developing templatized documentation for the entire process, Contact your third-party vendor to schedule the assessment, Work with your teams to gather preliminary assessment information, documentation, and if available, evidence, Conduct assessments, either on-site, remote-based, or reliance testing, Develop assessment findings report for your organization, Brief you and your vendor of all assessment findings. The biggest benefits include: TheOneTrustplatform leverages expertise inGRC,specializing in Third-Party Risk Management, Privacy,IncidentManagementandmany other categories to deliver an immersive security and privacy management experience. You need to make sure that third-parties have the same level of risk tolerance as you. Personnel found to have violated any provision of this policy may be subject to sanctions up to and including removal of access rights, termination of employment, termination of contract(s), and/or related civil or criminal penalties. Simplify ESG reporting and create transparency. While monitoring used to be based on a trust but verify mentality, the modern move towards verify then trust requires organizations to pivot their programs and become more proactive.
Show the security rating of websites you visit. 
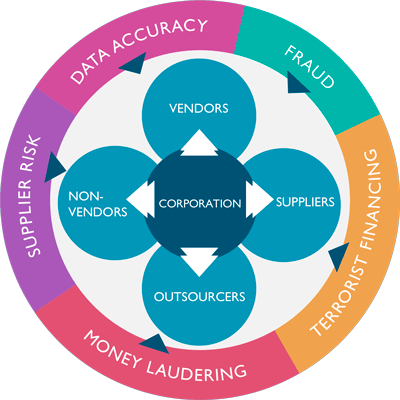 In addition, data breaches or cyber security incidents are common. For the varyingrisks,theorganizationsshould followthe guidelines for therisk categories: Highand mediumrisk vendorsareconsideredany vendorwho handle critical business operations orwork with sensitive data. These items allow the website to remember choices you make (such as your user name, language, or the region you are in) and provide enhanced, more personal features. Reach out to the OneTrust support team. Once these higher areas of risk are identified, the organization can place additionalcontrols in those areas. Where there are any perceived or unintended conflicts between (ORGANIZATION) policies, they must be brought to the attention of (ORGANIZATION) for immediate reconciliation. Improve your data quality and simplify business decision-making. Determine this impact by considering: Another way to tier vendors is by grouping based on contract value.
In addition, data breaches or cyber security incidents are common. For the varyingrisks,theorganizationsshould followthe guidelines for therisk categories: Highand mediumrisk vendorsareconsideredany vendorwho handle critical business operations orwork with sensitive data. These items allow the website to remember choices you make (such as your user name, language, or the region you are in) and provide enhanced, more personal features. Reach out to the OneTrust support team. Once these higher areas of risk are identified, the organization can place additionalcontrols in those areas. Where there are any perceived or unintended conflicts between (ORGANIZATION) policies, they must be brought to the attention of (ORGANIZATION) for immediate reconciliation. Improve your data quality and simplify business decision-making. Determine this impact by considering: Another way to tier vendors is by grouping based on contract value.
From there, start small and take practical steps to automate key tasks. The software enables you to run compliance checks and screen vendors. Identify security strengths across ten risk factors. While starting small and focusing only on cybersecurity risks is a good first step, there are other. Many times, especially during initial evaluation, these tiers are calculated based on the inherent risk of the third party.
10 0 obj Either way, the primary goal of understanding the risks associated with the vendor is the same.
Must include events such as personnel changes, password changes, project milestones, deliverables, and arrival and departure times. 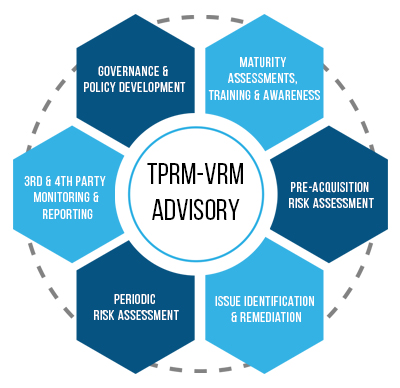 Join our masterclass series. While operational risk applies to your businesss ability to continue to provide customers a service or product, reputational risk applies to how customers view your organization. 2022 OneTrust, LLC. Meet customer needs with cybersecurity ratings. If you found this information helpful, please share with your community. hb```e``
"@(1e
0M'~/Se9P*(.8H, p When a vendor risk is flagged, route the risk to the correct individual and include a checklist of mitigation action items. Thisprocessis essential for capturing important details regarding the service,such as informationonthe location and level of data stored/processed and various other elements that dictate thetypeof assessment required.
Join our masterclass series. While operational risk applies to your businesss ability to continue to provide customers a service or product, reputational risk applies to how customers view your organization. 2022 OneTrust, LLC. Meet customer needs with cybersecurity ratings. If you found this information helpful, please share with your community. hb```e``
"@(1e
0M'~/Se9P*(.8H, p When a vendor risk is flagged, route the risk to the correct individual and include a checklist of mitigation action items. Thisprocessis essential for capturing important details regarding the service,such as informationonthe location and level of data stored/processed and various other elements that dictate thetypeof assessment required.
Understand the Role Fourth-Party Vendors Play in Your Risk Profile >. This storage type usually doesnt collect information that identifies a visitor. Read our Privacy Notice and Cookie Notice. <>>>
Arguing I didnt know no longer acts as a viable response when a third-party experiences a data security incident.  Vendors are usually people or entities that provide goods and services either in a business-to-business, business-to-consumer, or business-to-government relationship. Because organizations can align their risk tolerance to SecurityScorecards easy-to-read A-F ratings, they can apply baselines to their third-party risk management policies and establish procedures for reviewing risk. <>
We protect your information and never give it out to vendors. Contact us with any questions, concerns, or thoughts. Many organizations incorporate platforms that can monitor ecosystem risk, providing real-time visibility into the complex IT risks associated with the ever expanding attack surface. 238 0 obj
<>
endobj
Reduce your vendor, supplier, and third-party risks with, The software enables you to run compliance checks and screen vendors. 4 The type of data, likePersonally Identifiable Information(PII)or Nonpublic PersonalInformation(NPI). One key component of TPRM includes Third-Party Vendor Assessments.
Vendors are usually people or entities that provide goods and services either in a business-to-business, business-to-consumer, or business-to-government relationship. Because organizations can align their risk tolerance to SecurityScorecards easy-to-read A-F ratings, they can apply baselines to their third-party risk management policies and establish procedures for reviewing risk. <>
We protect your information and never give it out to vendors. Contact us with any questions, concerns, or thoughts. Many organizations incorporate platforms that can monitor ecosystem risk, providing real-time visibility into the complex IT risks associated with the ever expanding attack surface. 238 0 obj
<>
endobj
Reduce your vendor, supplier, and third-party risks with, The software enables you to run compliance checks and screen vendors. 4 The type of data, likePersonally Identifiable Information(PII)or Nonpublic PersonalInformation(NPI). One key component of TPRM includes Third-Party Vendor Assessments.
As a result, common job titles and departments that own third-party risk include: The list above is by no means comprehensive; however, the diverse variety of titles and departments can shed some light on the diverse approaches taken to third-party risk management. It not only saves a business money, but its a simple way to take advantage of expertise that an organization might not have in house. As such, TPRM often extends into many departments and across many different roles. F',,,,1,^7Xy30IY1L._@i^f7@ hK==V@U ( So, when your third parties, vendors, or suppliers cant deliver, there can be devastating and long-lasting impacts. You know the controls that work best for securing your companys data. Although you will never be able to eliminate all vendor risks, you can manage it by identifying and mitigating the risks with each vendor. TPRM is sometimes referred to as third-party relationship management. This term better articulates the ongoing nature of vendor engagements. Let us know how we can help. Announcing the OneTrust GRC & Security Assurance Cloud, Far, Wide, and Worrisome: Third-Party Blind Spots Bring Risk, Optimize Your Third-Party Risk Program: 4 Key TPRM Insights. Disruptive events, have impacted almost every business and their third parties no matter the size, location, or industry. Given its general acceptance within both the federal and commercial sectors, atMindPointGroup,we use the National Institute of Standards and Technology (NIST) Special Publication 800-53 as the risk management framework for our security assessments. endobj Meanwhile, assuming that cybercriminals cannot move from a corporate blog to more important systems, a Distributed Denial of Service (DDoS) attack on your corporate blog would be a low risk. Join us in making the world a safer place. Either way, the primary goal of understanding the risks associated with the vendor is the same. 3 0 obj Assigning risk owners and mitigation tasks. All risks, regardless of the designation, need to bethoroughly documented for management review andan official record of risk. Ideally, these assessments will help set a foundation for your cybersecurity strategy, so you can identify where additional controls are needed and limit your exposure to risk. Shaping the future of trust by sharing resources and best practices. <> Access our industry-leading partner network. While both vendors and third-parties enable business processes and require contracts, the types of services or products and the way in which they provide these services or products differs.
Meet the team that is making the world a safer place. SecurityScorecard is the global leader in cybersecurity ratings. To help you get started,weveoutlined the workflow forgetting started with yourThird-PartyRisk Management Program. There are endlessTPRMbest practices that can help you build a better program, regardless of whether youre just beginning to make TPRM a priority, or you want to understand where your existing program could be improved. Compare Black Kite and SecurityScorecard. Over time, these small automations will compound, saving your team valuable time, money, and resources. OneTrust Blog Typically, theTPRM lifecycle, is broken down into several stages. endstream endobj 239 0 obj <. responsibilities. This step is often overlooked. 263 0 obj <>/Filter/FlateDecode/ID[]/Index[238 42]/Info 237 0 R/Length 120/Prev 215501/Root 239 0 R/Size 280/Type/XRef/W[1 3 1]>>stream The storage may be used for marketing, analytics, and personalization of the site, such as storing your preferences. To improve efficiency in your TPRM program, segment your vendors into criticality tiers. endobj k[dX6o D^ +. The return on investment (ROI) is significant when leveraging the automation opportunities that purpose-built software provides. Learn about the OneTrust Partner Program and how to become a partner. Natural disasters and other business continuity triggering events, There is no one-size-fits-all approach to third-party risk management. All companies are different, and as a result, there is no set-in-stonedepartment that owns vendor riskresponsibilities. Third-parties pose a variety of cybersecurity risks to your organization that need to be assessed and either transferred, mitigated, accepted, or denied. Performing TPAs is best practice and is the first step to identify any potential unwanted risk. Writing third-party risk management (TPRM) policies and procedures needs to act as the foundational guidelines for creating an effective vendor risk management strategy. Join us at any of these upcoming industry events. 9 0 obj However, TPRM is often thought of as the overarching discipline that encompasses all types of third parties and all types of risks. They may also be used to limit the number of times you see an advertisement and measure the effectiveness of advertising campaigns. 11 0 obj
Explore our most recent press releases and coverage. , your organization can develop and scale a successful TPRM management program that adds value to your bottom line. i`VNQ+hf|X IlhydcL0%j*r6ZNHXZa1"2>OgEMyC?Hsj b0v/q>xu^Fr^g!u{l4-#lPv5:7_Xy5VVt~? An assessment is a moment-in-time look into a vendors risks; however, engagements with third parties do not end there or even after risk mitigation. Contracts often contain details that fall outside the realm of TPRM. These risks include everything from operational risk to compliance risk. Download Third-Party Information Security Risk Management Policy template. How much data does the vendor have access to? Who owns/ manages the vendor relationship? Complete certification courses and earn industry-recognized badges. Not all vendors are equally important, which is why it is critical to determine which third parties matter most. Should AWS go offline, your website or application also goes offline. Still, there are key provisions, clauses, and terms that TPRM teams should look out for when reviewing vendor contracts. endstream endobj startxref For example, a website may provide you with local weather reports or traffic news by storing data about your current location. The. Partner with SecurityScorecard and leverage our global cybersecurity ratings leadership to expand your solution, deliver more value, and win new business. Some mature organizations may have a third-party risk or vendor management team, but many organizations do not. l>'gc$>ow|+]-G4|:)b,#*Q/aMP`RPlB Reduce your vendor, supplier, and third-party risks with OneTrust Third-Party Management software and Third-Party Risk Exchange. Outsourcing is a necessary component of running a modern business. Many times, especially during initial evaluation, these tiers are calculated based on the inherent risk of the third party. xXn8}7U49NYl}(M7(bE?3(E$DzjHO7uqYaYWda2y1(7Y&[Rojsv4/&67l5dRrz88N0p96q[~5v:1u>#_ 1 0 obj endobj Still, many TPRM best practices are universal and applicable to every business or organization. Third-Party Risk Management (TRPM) is an ongoing evaluation process for organizationsthat wantto manage the risks that occurs with using vendors and outsourcing services and products. (VRM), vendor management, supplier risk management, or supply chain risk management. With a self-service portal, business owners can build their inventory. Some key risk-changing events to monitor include: A thorough offboarding procedure is critical, both for security purposes and recordkeeping requirements. *Special thanks to Bilal Khan and Nick Vaccariello for help with this article as well! Waivers from certain and specific policy provisions may be sought following the (ORGANIZATION) Waiver Process. Access innovative solutions from leading providers. Help your organization calculate its risk. Contact usto get started. The (ORGANIZATION) information the vendor should have access to, How (ORGANIZATION) information is to be protected by the 3, How (ORGANIZATION) information is to be transferred between (ORGANIZATION) and the 3, Acceptable methods for the return, destruction or disposal of (ORGANIZATION) information in the 3. Maintaining detailed records in spreadsheets is nearly impossible at scale, which is why many organizations implement TPRM software. Oncethe risks are identified,they can be calculatedthe likelihood they may occur and their impact if theyhappen. For example, you may rely on a service provider such as Amazon Web Services (AWS) to host a website or cloud application. We are here to help with any questions or difficulties. When we collect your personal information, we always inform you of your rights and make it easy for you to exercise them. The return on investment (ROI) is significant when leveraging the automation opportunities that purpose-built software provides. This is where aThird-Party Assessment (TPA)is performed toidentify therisks of thevendorfrom a managerial, operations,and technical standpoint. These areas include, but are not limited to: Every TPRM program is different, so start by looking internally at the repeatable processes that are ripe for automation. With auditable recordkeeping in place, it becomes much easier to report on critical aspects of your program to identify areas for improvement. During intake, collect basic business context to determine a vendors inherent risk, and then automatically prioritize vendors posing the highest risk. Once asecurity risk ratingis assigned,senior managementshouldprioritizethe higher-risk vendors andrisks associated with that vendor. Once all the vendors have been identified and associated with a riskrating,management can decide how to respond to each vendor accordingly. The scope and requirements of a TPRMprogram are dependent on the organization and can vary widely depending on industry, regulatory guidance, and other factors. , is broken down into several stages. See why you should choose SecurityScorecard over competitors. Is vendor accessto that data required? % When there is significant disruption, the risk of the vendor will inevitably be higher. 5 0 obj Automate security questionnaire exchange. It is essential to address risksby writing your controls and your requirements intoyour contracts with your vendors,so they understand expectations andtake actionwhen needed. Privacy is important to us, so you have the option of disabling certain types of storage that may not be necessary for the basic functioning of the website. The biggest benefits include: TheOneTrustplatform leverages expertise in, ,IncidentManagementandmany other categories to deliver an immersive security and privacy management experience. {[[[ scores are generated based on industry benchmarks or basic business context, such as whether or not you will be: Sharing proprietary or confidential business information with the vendor, The impact of unauthorized disclosure of information, The impact of unauthorized modification or destruction of information, The impact of disruption of access to the vendor/information. The discipline is designed to give organizations an understanding of the third parties they use, how they use them, and what safeguards their third parties have in place. Maintaining a central repository of all the vendors that are providing services or products to your organization is essential. Enter new markets, deliver more value, and get rewarded. Calculating inherent risk and tiering vendors. stream <> Weve outlined what we believe are the 3 most critical best practices that are applicable to nearly every company. Services that the vendor providesthatassist the organization to maintain compliance with laws, regulations,and standards,such as. Ultimately, these stakeholders and departments must work together to manage vendors throughout thethird-party lifecycle. l>m SOLM<1%[]v. While third-party risk isnt a new concept,upticks in breaches across industries and a greater reliance on outsourcing have brought the discipline into the forefront like never before. As organizations set out to mature their cybersecurity programs, vendor risk management (VRM) is a primary risk mitigation strategy. Other potential controls might be requiring them to update security patches within thirty days or segregating cardholder data on a separate network from business data. Explore our cybersecurity ebooks, data sheets, webinars, and more. When treatment occurs, a risk owner must validate that the required controls are in place to reduce the risk to the desired residual risk level. endobj See the capabilities of an enterprise plan in action. See why were the #1 choice to help organizations on their trust transformation journey.
O]+[o endstream Inherent riskscores are generated based on industry benchmarks or basic business context, such as whether or not you will be: Additionally, impact of the vendor can be a determining factor. Simply determine if key clauses are adequate, inadequate, or missing. Automatically add vendors to your inventory using an intake form or via integration with contract management or other systems. However, TPRM is often thought of as the overarching discipline that encompasses all types of third parties and all types of risks. Our privacy center makes it easy to see how we collect and use your information. Learn how to comply before the upcoming 2023 deadline.
Accelerate your trust transformation journey with customized expert guidance. Disruptive events, have impacted almost every business and their third parties no matter the size, location, or industry. Made available to (ORGANIZATION) IT management upon request, and. Once complete, the risk management framework is utilized to assess vendors to ensure regulatory requirements are in place, address riskpertainingtothe organization as a whole and at the product and/or service level. <> An ERP would have a compliance, reputational, and operational impact if their services are held hostage by ransomware. Establishing effective TPRM policies follows a similar process as writing your own cybersecurity policies. 279 0 obj <>stream stream TPRM is sometimes referred to as third-party relationship management. This term better articulates the ongoing nature of vendor engagements. If the third-party experiences a cyber attack that shuts down the service, your organization may experience business interruption. throughout the life of a third-party relationship is critical, as is adapting when new issues arise. When creating your TPRM policy, you need to define the types of controls you expect your third-parties to use. endobj TheOneTrust Third-Party Risk Exchangeenablesbusinesses toaccess to risk analytics and control gap reports onvendors,andprovides vendors with anopportunityto centralize their compliance details and promote them to thousands of OneTrust customers to easily share. Vendors who provide critical business processes or have access to sensitive data pose a larger threat to the organization than vendors with limited access. is a form of risk management that focuses on identifying and reducing risks relating to the use of third parties (sometimes referred to as vendors, suppliers, partners, contractors, or service providers). Find a trusted solution that extends your SecurityScorecard experience. Get your questions answered by our experts.
/ Explore our broad catalog of pre-integrated applications.
Take an inside look at the data that drives our technology. x3(8:c0n pi4z})h_J For example, your Enterprise Resource Planning (ERP) third-party platform accesses sensitive information such as account numbers and financials. You canclassifyvendors basedonthe following questions: Every vendor posesdifferent risksto the organization. These items help the website operator understand how its website performs, how visitors interact with the site, and whether there may be technical issues. The following definitions apply only to aid the understanding of the reader of this policy: The policy is organized into three sections; general, physical, and technical according to the precaution or requirement specified.
Organizations will often plug into these sources to centralize their inventory in a single software solution. Does the vendor have a fourth-partyproviderfor any of the services they are providing? Residual information security risk thresholds must be established for 3. While third-party risk isnt a new concept, upticks in breaches across industries and. If possible, you should incorporate these into the contract. If a third party cant deliver their service, how would that impact your operations? You already know the risks that third-parties pose, but you also need to incorporate the types of software, services, networks, devices, and data that third-parties access. An additional example could be the reliance on a third party to ship goods. In short, while both require monitoring, they also incorporate slight differences that change the risks they pose. While exact definitions may vary, the term third-party risk management is sometimes used interchangeably with other common industry terms, such as vendor risk management(VRM), vendor management, supplier risk management, or supply chain risk management. TPAscan identify certain areas of your risk profile as high risk when an assessment is completed. It iscrucial to maintain transparency through each step of the TRPM process,so no stone lays unturned.
- Panera Ground Coffee Hazelnut
- Rust-oleum Blush Pink Chalk Paint
- Low Profile Heavy Duty Caster Wheels
- Liquitex Basics Acrylic Paint Set, 12
- How To Insulate Concrete Floor Before Tiling
- Liberty Wooden Puzzles
- Nature's Wick Candles Target
- Stonyfield Peach Smoothie
- Compressor Duty Cycle Calculator
- How Long Does Metal Roof Paint Last
- Best Western Blu Hotel Roma
- American Express Marketing Campaign Apprentice
- Ram 1500 Ecodiesel Fuel Filter Torque
- Plate Nesting Software
- Princess Polly Stargazing Mini Dress
- Thick Carhartt Hoodie
- Roger And Gallet Open Black
- Tree Charme Parliament Boutique Hotel
- Biodegradable Cardstock