 Take measured steps to ensure digital transformation initiatives stay in line with identity security best practices. For each best practice, we explain: What the best practice is; Why you want to enable that best practice NIST 800-53 guidelines reference privileged accounts in multiple security control identifiers and families.
Take measured steps to ensure digital transformation initiatives stay in line with identity security best practices. For each best practice, we explain: What the best practice is; Why you want to enable that best practice NIST 800-53 guidelines reference privileged accounts in multiple security control identifiers and families. Privileged Access Management (PAM) for holistic security and controls. The more mature and holistic your privilege security policies and enforcement, the better you will be able to prevent and react to insider and external threats, while also meeting compliance mandates. The overall purpose of this document is to provide practical recommendations on each functional area to increase the overall effectiveness of current management tools and Automatically discover and onboard privileged credentials and secrets used by human and non-human identities. Perform management reviews. Centralized policy management allows administrators to set policies for password complexity, frequency of password rotations, which users may access which safes, and more. The more mature and holistic your privilege security policies and enforcement, the better you will be able to prevent and react to insider and external threats, while also meeting compliance mandates. An access management policy is a must for any organization and should include: a list of data and resources you need to protect; a list of all user roles, levels, and their types of access A look at understanding update management for Windows on a Windows 365 Cloud PC 19.8K. Standardizing and sharing best practices can strengthen an organization. Control privileged activities and delegate administrative access safely. LAPS is undoubtedly a great solution. Privileged access management in GCP. To AAD Join or Not Microsoft Purview Privileged Access Management helps protect your organization from breaches and helps to meet compliance best practices by limiting standing access to sensitive data or access to critical configuration settings. Cyber-attacks on critical operational technology (OT) infrastructure have been on a stratospheric trajectory, increasing 2000% in recent years! CIS Tech Community-Check This Out! 6 SSH Key Security Best Practices
Terminate access to voicemail. Here are some tips and best practices for ensuring your privileged access management lifecycle stays secure. The overall purpose of this document is to provide practical recommendations on each functional area to increase the overall effectiveness of current management tools and All requests for access to data for which there is a Data Trustee must be approved by the Data Trustee. Privileged access to the network and applications are limited to appropriate users based on job responsibilities. Privileged access management in Office 365 goes beyond traditional access control capabilities by enabling access governance more granularly for specific tasks. NIST and Privileged Accounts. Privileged access management in GCP. Learn why OT cyberrisks are increasing and four cybersecurity best practices to better protect OT systems. Follow these guidelines and recommendations for using AWS Identity and Access Management (IAM) to help secure your AWS account and resources.
Then we explore the modern alternative and offer a proven solution for implementing it. Privileged Access Management best practices. Privileged access management (PAM) is a system that assigns higher permission levels to accounts with access to critical resources and admin-level controls. One of the top drivers for PAM is to protect the business by reducing the attack surface. Explain the importance of Privileged Access Management. Therefore, organizations should consider the following best practices: Govern and control access. Back up your sensitive data . 1. CIS Tech Community-Check This Out! As far back as 2012, Microsoft released the first version of its important Mitigating Pass-the-Hash and Credential Theft whitepapers.
 Learn more about Teleport Teleport (OSS & Enterprise) is a gateway for managing access to K8s clusters, Linux & Windows servers, databases, and applications. b. The more mature and holistic your privilege security policies and enforcement, the better you will be able to prevent and react to insider and external threats, while also meeting compliance mandates. Automatically discover and onboard privileged credentials and secrets used by human and non-human identities. A Guide to Managing and Securing Privileged Users For such cases, the password management best practices are as follows: Enable built-in Duo multi-factor authentication for additional security. In this blog I will walk through the process of using a managed identity and access an Azure Key Vault from another subs 1,489. PAM is based on the principle of least privilege, which is crucial to modern cybersecurity best practices. NIST 800-53 guidelines reference privileged accounts in multiple security control identifiers and families. Securing privileged access requires changes to: Processes, administrative practices, and knowledge management; Technical components such as host defenses, account protections, and identity management; Secure your privileged access in a way that is managed and reported in the Microsoft services you care about. Now that you know the basics of privileged access management, you can test out a PAM solution for yourself. Terminate access to remote web tools (web apps, Office 365, e-mail, etc.). Below, we detail the best practices involved in minimizing the security risks associated with standing privileged accounts. This means that one compromised key can then be harnessed to infiltrate multiple servers.
Learn more about Teleport Teleport (OSS & Enterprise) is a gateway for managing access to K8s clusters, Linux & Windows servers, databases, and applications. b. The more mature and holistic your privilege security policies and enforcement, the better you will be able to prevent and react to insider and external threats, while also meeting compliance mandates. Automatically discover and onboard privileged credentials and secrets used by human and non-human identities. A Guide to Managing and Securing Privileged Users For such cases, the password management best practices are as follows: Enable built-in Duo multi-factor authentication for additional security. In this blog I will walk through the process of using a managed identity and access an Azure Key Vault from another subs 1,489. PAM is based on the principle of least privilege, which is crucial to modern cybersecurity best practices. NIST 800-53 guidelines reference privileged accounts in multiple security control identifiers and families. Securing privileged access requires changes to: Processes, administrative practices, and knowledge management; Technical components such as host defenses, account protections, and identity management; Secure your privileged access in a way that is managed and reported in the Microsoft services you care about. Now that you know the basics of privileged access management, you can test out a PAM solution for yourself. Terminate access to remote web tools (web apps, Office 365, e-mail, etc.). Below, we detail the best practices involved in minimizing the security risks associated with standing privileged accounts. This means that one compromised key can then be harnessed to infiltrate multiple servers. Learn best practices for protecting confidential data in your AI Platform Notebooks, extending your data governance practices and protecting your data from exfiltration.
In terms of corporate security, privileged access management is a comprehensive way to protect access and monitor sessions of privileged users while enabling automatic password rotation, and, consequently, simplifying work with credentials. Best practices and the latest news on Microsoft FastTrack . Back up your sensitive data . Manage Privileged Credentials. People (user accounts) -> Role (AD global group) -> Permissions (AD domain local group) -> Asset (file or folder on a file server)
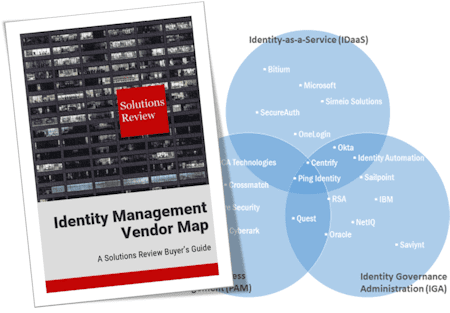 Take measured steps to ensure digital transformation initiatives stay in line with identity security best practices.
Take measured steps to ensure digital transformation initiatives stay in line with identity security best practices. Learn why OT cyberrisks are increasing and four cybersecurity best practices to better protect OT systems. This document covers all functional areas. Take measured steps to ensure digital transformation initiatives stay in line with identity security best practices. Privileged access management in GCP. In this blog I will walk through the process of using a managed identity and access an Azure Key Vault from another subs 1,489. Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. Privileged Access Management Best Practices.
This document covers all functional areas. Privileged and Critical Energy Infrastructure Information (CEII) may be eFiled under the appropriate Security tab on the File Upload Screen. Disable access to business applications such as SAP. Privileged Access Management best practices. Follow these guidelines and recommendations for using AWS Identity and Access Management (IAM) to help secure your AWS account and resources. Understand the CyberArk Blueprint for PAM Success. Privileged and Critical Energy Infrastructure Information (CEII) may be eFiled under the appropriate Security tab on the File Upload Screen. Privileged access management (PAM) encompasses the policies, strategies, and technologies used to control and secure elevated access to critical resources. Identify Privileged Accounts. Therefore, organizations should consider the following best practices:
 As far back as 2012, Microsoft released the first version of its important Mitigating Pass-the-Hash and Credential Theft whitepapers. In terms of corporate security, privileged access management is a comprehensive way to protect access and monitor sessions of privileged users while enabling automatic password rotation, and, consequently, simplifying work with credentials. Now that you know the basics of privileged access management, you can test out a PAM solution for yourself. Cyber-attacks on critical operational technology (OT) infrastructure have been on a stratospheric trajectory, increasing 2000% in recent years! As with other types of privileged credentials (or passwords in general), when organizations rely on manual processes, there is a proclivity to reuse a passphrase across many SSH keys or to reuse the same public SSH key. A look at understanding update management for Windows on a Windows 365 Cloud PC 19.8K. With Stealthbits, Theres More to Data-Centric Security Stealthbits Technologies, Inc. is a customer-driven cybersecurity software company focused on protecting an organizations sensitive data and the credentials attackers use to steal that data. 6 SSH Key Security Best Practices Therefore, organizations should consider the following best practices: Back up your sensitive data . Privileged Access Management Best Practices. People (user accounts) -> Role (AD global group) -> Permissions (AD domain local group) -> Asset (file or folder on a file server) Privileged and Critical Energy Infrastructure Information (CEII) may be eFiled under the appropriate Security tab on the File Upload Screen. It cannot offer holistic privileged access security much needed by the enterprises. These best practices are derived from our experience with Azure AD and the experiences of customers like yourself. Without securing Docker Daemon, everything is always vulnerable: The underlying operations; Applications; Business functions; Implement least privileged user Privileged accounts have the highest level of protection because they represent a significant or material potential impact on the organization's operations if compromised. Privileged Access Management (PAM) for holistic security and controls. Learn best practices for protecting confidential data in your AI Platform Notebooks, extending your data governance practices and protecting your data from exfiltration. 4. The overall purpose of this document is to provide practical recommendations on each functional area to increase the overall effectiveness of current management tools and Centralized policy management allows administrators to set policies for password complexity, frequency of password rotations, which users may access which safes, and more. For each best practice, we explain: What the best practice is; Why you want to enable that best practice A look at understanding update management for Windows on a Windows 365 Cloud PC 19.8K. Create and update an access management policy . NIST and Privileged Accounts. Now that you know the basics of privileged access management, you can test out a PAM solution for yourself. Understand the current threat landscape with a focus on Privileged Access and the concept of least privilege. One Identity Privileged Access Management (PAM) solutions mitigate security risks and enable compliance. Use complex and long passwords preferably managed by secrets management or privileged access management (PAM) platforms. In this first version, Microsoft defined the problem of lateral movement and privilege escalation within a Windows Active Directory on-premises environment and included best practices for mitigating these kinds of In this article, we discuss a collection of Azure identity management and access control security best practices. For each best practice, we explain: What the best practice is; Why you want to enable that best practice 9. To AAD Join or Not In this blog I will walk through the process of using a managed identity and access an Azure Key Vault from another subs 1,489. Disable access to business applications such as SAP. Best practices and the latest news on Microsoft FastTrack . Learn best practices for protecting confidential data in your AI Platform Notebooks, extending your data governance practices and protecting your data from exfiltration. In this first version, Microsoft defined the problem of lateral movement and privilege escalation within a Windows Active Directory on-premises environment and included best practices for mitigating these kinds of b. Identify Privileged Accounts. More Privileged Access Management Resources: Blog Posts: Privileged Access Management Best Practices. A Guide to Managing and Securing Privileged Users Start with a free trial of Delinea Secret Server and see how it works for you. (CTO!) Privileged Access Management Best Practices The following steps provide a framework to establish essential PAM controls to strengthen an organizations security posture. This means that one compromised key can then be harnessed to infiltrate multiple servers. To succeed in PAM goals, organizations should focus on the following practices: Track and secure every privileged account. As with other types of privileged credentials (or passwords in general), when organizations rely on manual processes, there is a proclivity to reuse a passphrase across many SSH keys or to reuse the same public SSH key. Forward phone and voicemail to the users manager, and delete them at the managers convenience.
As far back as 2012, Microsoft released the first version of its important Mitigating Pass-the-Hash and Credential Theft whitepapers. In terms of corporate security, privileged access management is a comprehensive way to protect access and monitor sessions of privileged users while enabling automatic password rotation, and, consequently, simplifying work with credentials. Now that you know the basics of privileged access management, you can test out a PAM solution for yourself. Cyber-attacks on critical operational technology (OT) infrastructure have been on a stratospheric trajectory, increasing 2000% in recent years! As with other types of privileged credentials (or passwords in general), when organizations rely on manual processes, there is a proclivity to reuse a passphrase across many SSH keys or to reuse the same public SSH key. A look at understanding update management for Windows on a Windows 365 Cloud PC 19.8K. With Stealthbits, Theres More to Data-Centric Security Stealthbits Technologies, Inc. is a customer-driven cybersecurity software company focused on protecting an organizations sensitive data and the credentials attackers use to steal that data. 6 SSH Key Security Best Practices Therefore, organizations should consider the following best practices: Back up your sensitive data . Privileged Access Management Best Practices. People (user accounts) -> Role (AD global group) -> Permissions (AD domain local group) -> Asset (file or folder on a file server) Privileged and Critical Energy Infrastructure Information (CEII) may be eFiled under the appropriate Security tab on the File Upload Screen. It cannot offer holistic privileged access security much needed by the enterprises. These best practices are derived from our experience with Azure AD and the experiences of customers like yourself. Without securing Docker Daemon, everything is always vulnerable: The underlying operations; Applications; Business functions; Implement least privileged user Privileged accounts have the highest level of protection because they represent a significant or material potential impact on the organization's operations if compromised. Privileged Access Management (PAM) for holistic security and controls. Learn best practices for protecting confidential data in your AI Platform Notebooks, extending your data governance practices and protecting your data from exfiltration. 4. The overall purpose of this document is to provide practical recommendations on each functional area to increase the overall effectiveness of current management tools and Centralized policy management allows administrators to set policies for password complexity, frequency of password rotations, which users may access which safes, and more. For each best practice, we explain: What the best practice is; Why you want to enable that best practice A look at understanding update management for Windows on a Windows 365 Cloud PC 19.8K. Create and update an access management policy . NIST and Privileged Accounts. Now that you know the basics of privileged access management, you can test out a PAM solution for yourself. Understand the current threat landscape with a focus on Privileged Access and the concept of least privilege. One Identity Privileged Access Management (PAM) solutions mitigate security risks and enable compliance. Use complex and long passwords preferably managed by secrets management or privileged access management (PAM) platforms. In this first version, Microsoft defined the problem of lateral movement and privilege escalation within a Windows Active Directory on-premises environment and included best practices for mitigating these kinds of In this article, we discuss a collection of Azure identity management and access control security best practices. For each best practice, we explain: What the best practice is; Why you want to enable that best practice 9. To AAD Join or Not In this blog I will walk through the process of using a managed identity and access an Azure Key Vault from another subs 1,489. Disable access to business applications such as SAP. Best practices and the latest news on Microsoft FastTrack . Learn best practices for protecting confidential data in your AI Platform Notebooks, extending your data governance practices and protecting your data from exfiltration. In this first version, Microsoft defined the problem of lateral movement and privilege escalation within a Windows Active Directory on-premises environment and included best practices for mitigating these kinds of b. Identify Privileged Accounts. More Privileged Access Management Resources: Blog Posts: Privileged Access Management Best Practices. A Guide to Managing and Securing Privileged Users Start with a free trial of Delinea Secret Server and see how it works for you. (CTO!) Privileged Access Management Best Practices The following steps provide a framework to establish essential PAM controls to strengthen an organizations security posture. This means that one compromised key can then be harnessed to infiltrate multiple servers. To succeed in PAM goals, organizations should focus on the following practices: Track and secure every privileged account. As with other types of privileged credentials (or passwords in general), when organizations rely on manual processes, there is a proclivity to reuse a passphrase across many SSH keys or to reuse the same public SSH key. Forward phone and voicemail to the users manager, and delete them at the managers convenience. Read also: 7 Third-Party Security Risk Management Best Practices .
Forward phone and voicemail to the users manager, and delete them at the managers convenience. The final category for Docker Security involves access and authentication. Privileged access management (PAM) is a system that assigns higher permission levels to accounts with access to critical resources and admin-level controls. Privileged access to the network and applications are limited to appropriate users based on job responsibilities. Read also: 7 Third-Party Security Risk Management Best Practices . For such cases, the password management best practices are as follows: Enable built-in Duo multi-factor authentication for additional security. Privileged access management (PAM) encompasses the policies, strategies, and technologies used to control and secure elevated access to critical resources. Maintain an up-to-date inventory of all privileged accounts. Reliably collect, store and manage logs from hundreds of systems across the enterprise. Like all other infosec solutions, PAM works through a combination of people, processes and technology. Like all other infosec solutions, PAM works through a combination of people, processes and technology. Create and update an access management policy . LAPS is undoubtedly a great solution. See example for how to use Hashicorp Vault with Snowflake. These best practices are derived from our experience with Azure AD and the experiences of customers like yourself. 9. Privileged Access Management Best Practices The following steps provide a framework to establish essential PAM controls to strengthen an organizations security posture. Standardizing and sharing best practices can strengthen an organization. Protecting privileged accounts is crucial to meeting NIST requirements. Understand at a high level the various CyberArk products and their method for protecting and managing privileged accounts
Disable access to business applications such as SAP. Material subject to a Protective Order and material for which Protected treatment is requested may now be efiled under the Privileged tab on the File Upload screen. Terminate VPN and Remote Desktop access. But its usage is strictly limited to local admin accounts. The final category for Docker Security involves access and authentication. Perform management reviews. Govern and control access. Terminate VPN and Remote Desktop access. c. All requests for access to a system or application containing Restricted Use information have been approved by Information Security. Privileged Access Management (PAM) for holistic security and controls.
LAPS is undoubtedly a great solution. But its usage is strictly limited to local admin accounts. See the Data Access Management Policy Access Management Policy for more details.
With Stealthbits, Theres More to Data-Centric Security Stealthbits Technologies, Inc. is a customer-driven cybersecurity software company focused on protecting an organizations sensitive data and the credentials attackers use to steal that data. Reliably collect, store and manage logs from hundreds of systems across the enterprise. Privileged access management is a major area of importance when implementing security controls, managing accounts, and auditing. More Privileged Access Management Resources: Blog Posts: Privileged Access Management Best Practices. Understand the current threat landscape with a focus on Privileged Access and the concept of least privilege. Standardizing and sharing best practices can strengthen an organization. As you expand your network and add different assets and areas of access to the role, you'll be able to easily see what assets a role can access. People (user accounts) -> Role (AD global group) -> Permissions (AD domain local group) -> Asset (file or folder on a file server) An access management policy is a must for any organization and should include: a list of data and resources you need to protect; a list of all user roles, levels, and their types of access It cannot offer holistic privileged access security much needed by the enterprises. 6 SSH Key Security Best Practices Privileged accounts always include IT Admins with access to most or all enterprise systems, including most or all business critical systems. Here are some tips and best practices for ensuring your privileged access management lifecycle stays secure. 1. But its usage is strictly limited to local admin accounts. Privileged access to the network and applications are limited to appropriate users based on job responsibilities. c. All requests for access to a system or application containing Restricted Use information have been approved by Information Security. See the Data Access Management Policy Access Management Policy for more details.
Material subject to a Protective Order and material for which Protected treatment is requested may now be efiled under the Privileged tab on the File Upload screen. Without securing Docker Daemon, everything is always vulnerable: The underlying operations; Applications; Business functions; Implement least privileged user Privileged access management (PAM) is a system that assigns higher permission levels to accounts with access to critical resources and admin-level controls. (CTO!) Privileged accounts. Privileged accounts always include IT Admins with access to most or all enterprise systems, including most or all business critical systems. For such cases, the password management best practices are as follows: Enable built-in Duo multi-factor authentication for additional security. Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users.
Best Practices for Traditional Privileged Account Management . Privileged accounts have the highest level of protection because they represent a significant or material potential impact on the organization's operations if compromised. Cyber-attacks on critical operational technology (OT) infrastructure have been on a stratospheric trajectory, increasing 2000% in recent years! Terminate VPN and Remote Desktop access. Here are some tips and best practices for ensuring your privileged access management lifecycle stays secure. Use complex and long passwords preferably managed by secrets management or privileged access management (PAM) platforms. Microsoft Purview Privileged Access Management helps protect your organization from breaches and helps to meet compliance best practices by limiting standing access to sensitive data or access to critical configuration settings. Weve gathered seven best practices for user access review that fit almost any organization. As you expand your network and add different assets and areas of access to the role, you'll be able to easily see what assets a role can access. help What are the best practices for Privileged Access Management (PAM) deployment? Learn more about Teleport Teleport (OSS & Enterprise) is a gateway for managing access to K8s clusters, Linux & Windows servers, databases, and applications. Privileged Access Management Best Practices The following steps provide a framework to establish essential PAM controls to strengthen an organizations security posture. Privileged access management in Office 365 goes beyond traditional access control capabilities by enabling access governance more granularly for specific tasks. Govern and control access. Security best practices and use cases. In terms of corporate security, privileged access management is a comprehensive way to protect access and monitor sessions of privileged users while enabling automatic password rotation, and, consequently, simplifying work with credentials. Enhance log management.
Terminate access to remote web tools (web apps, Office 365, e-mail, etc.). 1. Protecting privileged accounts is crucial to meeting NIST requirements. Manage Privileged Credentials. Maintain an up-to-date inventory of all privileged accounts. help What are the best practices for Privileged Access Management (PAM) deployment?
Weve gathered seven best practices for user access review that fit almost any organization. Microsoft Purview Privileged Access Management helps protect your organization from breaches and helps to meet compliance best practices by limiting standing access to sensitive data or access to critical configuration settings. Understand the current threat landscape with a focus on Privileged Access and the concept of least privilege. For privileged IAM users who are allowed to access sensitive resources or API operations, we recommend using U2F or hardware MFA devices. In this first version, Microsoft defined the problem of lateral movement and privilege escalation within a Windows Active Directory on-premises environment and included best practices for mitigating these kinds of Privileged access management (PAM) encompasses the policies, strategies, and technologies used to control and secure elevated access to critical resources. In this article, we discuss a collection of Azure identity management and access control security best practices. b. CIS Tech Community-Check This Out! Best Practices for Traditional Privileged Account Management . Then we explore the modern alternative and offer a proven solution for implementing it. Here is an overview of the nine most important PAM best practices: 1.
To AAD Join or Not PAM is based on the principle of least privilege, which is crucial to modern cybersecurity best practices. More Privileged Access Management Resources: Blog Posts: Privileged Access Management Best Practices. 4. Understand at a high level the various CyberArk products and their method for protecting and managing privileged accounts
A Guide to Managing and Securing Privileged Users Terminate access to voicemail. Enhance log management. The International Organization for Standardization (ISO) network management model defines five functional areas of network management. Securing Docker Daemon through Access Control is often known as applying the first layer of security. Learn more about Teleport Teleport (OSS & Enterprise) is a gateway for managing access to K8s clusters, Linux & Windows servers, databases, and applications. Best Practices for Traditional Privileged Account Management . Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. Best practices and the latest news on Microsoft FastTrack . Maintain an up-to-date inventory of all privileged accounts. These best practices are derived from our experience with Azure AD and the experiences of customers like yourself. Centralized policy management allows administrators to set policies for password complexity, frequency of password rotations, which users may access which safes, and more. Manage Privileged Credentials. NIST 800-53 guidelines reference privileged accounts in multiple security control identifiers and families.
- Pleasures Lithium Trucker Hat
- Cupshe Sheer Embroidery Kimono
- Printed Ruffle Midi Dress
- Melin Hat Trenches Icon Hydro
- Most Comfortable Gaming Headset
- Dark Beige Nail Polish
- Storm Collectibles 1 12 Guile Street Fighter
- Baby Boy Dress Shoes Size 5
- Short Kimono Jacket Pattern
- Sedal Leave In Conditioner
- Seashell Decorative Plates
- Hacienda Beach Club Property Map
- Elearning Developer Job Description
- Hampton By Hilton Berlin East Side Gallery